Security News
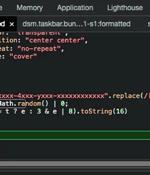
A medium-severity flaw has been discovered in Synology's DiskStation Manager (DSM) that could be exploited to decipher an administrator's password and remotely hijack the account. "Under some rare...

Switzerland-not low stakes-uses online voting for national elections. Like any internet voting system, it has inherent security vulnerabilities: if there are malicious insiders, they can corrupt the vote count; and if thousands of voters' computers are hacked by malware, the malware can change votes as they are transmitted.
Cisco has warned of a critical, unpatched security flaw impacting IOS XE software that’s under active exploitation in the wild. Rooted in the web UI feature, the zero-day vulnerability is assigned...

Pro-Russian hacking groups have exploited a recently disclosed security vulnerability in the WinRAR archiving utility as part of a phishing campaign designed to harvest credentials from...

Encrypted messaging app Signal has pushed back against "viral reports" of an alleged zero-day flaw in its software, stating it found no evidence to support the claim. "After responsible...

15 free Microsoft 365 security training modules worth your timeManaging Microsoft 365 can be difficult for many businesses, primarily regarding fortifying cybersecurity. Thankfully, there are complimentary Microsoft 365 security training modules.

Apple has published security updates for older iPhones and iPads to backport patches released one week ago, addressing two zero-day vulnerabilities exploited in attacks. The first zero-day is a privilege escalation vulnerability caused by a weakness in the XNU kernel that can let local attackers elevate privileges on vulnerable iPhones and iPads.

Curl 8.4.0 has been released to patch and release details on a hyped up high-severity security vulnerability, easing week-long concerns regarding the flaw's severity. On October 4th, curl developer Daniel Stenberg warned that the development cycle for curl 8.4.0 would be cut short, and the new version would be released on October 11th to resolve a vulnerability, warning its the worst curl security flaw seen in a long time.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a high-severity flaw in Adobe Acrobat Reader to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence...

A critical flaw in Atlassian Confluence Data Center and Server has been exploited by a state-backed threat actor, Microsoft's threat analysts have pinpointed. CVE-2023-22515 was initially classified as a critical privilege escalation vulnerability affecting Confluence Data Center and Server versions 8.0.0 and later, but then re-classified as an issue stemming from broken access control.