Security News

A new security shortcoming discovered in Apple M-series chips could be exploited to extract secret keys used during cryptographic operations. Dubbed GoFetch, the vulnerability relates to a...

Lynis: Open-source security auditing toolLynis is a comprehensive open-source security auditing tool for UNIX-based systems, including Linux, macOS, and BSD. WebCopilot: Open-source automation tool enumerates subdomains, detects bugsWebCopilot is an open-source automation tool that enumerates a target's subdomains and discovers bugs using various free tools. NIST's NVD has encountered a problemWhether the cause is insurmountable technical debt, lack of funds, a third reason or all of them, NIST's National Vulnerability Database is struggling, and it's affecting vulnerability management efforts.
Apple is having its own Meltdown/Spectre moment with a new side-channel vulnerability found in the architecture of Apple Silicon processors that gives malicious apps the ability to extract cryptographic keys. "We reverse-engineered DMPs on Apple m-series CPUs and found that the DMP activates data loaded from memory that 'looks like' a pointer," the team say in the paper.

Ivanti has disclosed details of a critical remote code execution flaw impacting Standalone Sentry, urging customers to apply the fixes immediately to stay protected against potential cyber...

Ivanti has fixed a critical RCE vulnerability in Ivanti Standalone Sentry that has been reported by researchers with the NATO Cyber Security Centre. The vulnerability affects all supported version of Ivanti Standalone Sentry as well as older, unsupported ones.

The Cyber Crime Center of the U.S. Department of Defense says it has reached the milestone of processing its 50,000th vulnerability report submitted by 5,635 researchers since its inception in November 2016. The federal agency launched its Vulnerability Disclosure Program 7.5 years ago following a bug bounty event called 'Hack-the-Pentagon,' to engage crowd-sourced vulnerability reports that could help bolster its cyber defenses.

Proof-of-concept exploit code for a critical RCE vulnerability in Fortra FileCatalyst MFT solution has been published.Fortra FileCatalyst is an enterprise managed file transfer software solution that includes several components: FileCatalyst Direct, Workflow, and Central.

Fortra has released details of a now-patched critical security flaw impacting its FileCatalyst file transfer solution that could allow unauthenticated attackers to gain remote code execution on...
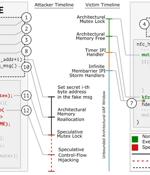
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the...

A recently fixed SQL injection vulnerability in Fortinet's FortiClient Endpoint Management Server solution has apparently piqued the interest of many: Horizon3's Attack Team means to publish technical details and a proof-of-concept exploit for it next week, and someone is attempting to sell a PoC for less than $300 via GitHub. "An improper neutralization of special elements used in an SQL Command vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute unauthorized code or commands via specifically crafted requests," the company's product security incident response team pithily states in the associated advisory.