Security News

Details have emerged about a new critical security flaw impacting PHP that could be exploited to achieve remote code execution under certain circumstances. The vulnerability, tracked as...

SolarWinds has fixed a high-severity vulnerability affecting its Serv-U managed file transfer server solution, which could be exploited by unauthenticated attackers to access sensitive files on the host machine. Serv-U MFT Server is a widely used enterprise solution that provides secure file transfer and file sharing hosted on Windows and Linux machines.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The vulnerability that allowed a German journalist to discover links to video conference meetings held by Bundeswehr and the Social Democratic Party of Germany via their self-hosted Cisco Webex instances similarly affected the Webex cloud service. "The cause of the vulnerability is again Cisco does not use random numbers to assign numbers used for meetings," Netzbegrünung explained.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
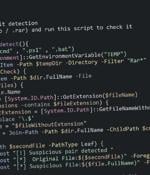
Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. "The FlyingYeti campaign...

The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting Palo Alto Networks firewalls to its exploit arsenal. The addition of the...

A maximum-severity security flaw has been disclosed in the TP-Link Archer C5400X gaming router that could lead to remote code execution on susceptible devices by sending specially crafted...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting Apache Flink, the open-source, unified stream-processing and batch-processing...