Security News
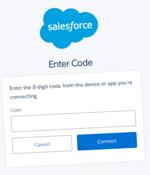
Google has disclosed details of a financially motivated threat cluster that it said "specialises" in voice phishing (aka vishing) campaigns designed to breach organizations' Salesforce instances...

In this Help Net Security video, Alexis Ober, Threat Intel Analyst at Fortra, discusses the threat actor group PlugValley, which is now offering AI-powered vishing-as-a-service. Rather than...

AI is making voice phishing (vishing) more dangerous than ever, with scammers cloning voices in seconds to trick employees into handing over their credentials. Learn how to defend your...

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: 48,000+ internet-facing Fortinet firewalls still open to attack Despite last week’s confirmation...

The “email bombing + posing as tech support via Microsoft Teams” combination is proving fruitful for two threat actors looking to deliver ransomware to organizations, and they seem to be ramping...

Protect your business from VoIP fraud. Learn how to recognize the most common types and harden your phone system security.

The CryptoChameleon phishing kit is being leveraged by vishing attackers looking to trick LastPass users into sharing their master password. "Initially, we learned of a new parked domain and immediately marked the website for monitoring should it go live and start serving a phishing site intended to imitate our login page or something similar. Once we identified that this site went active and was being used in a phishing campaign against our customers, we worked with our vendor to take down the site," LastPass intelligence analyst Mike Kosak explained.

76% of enterprises lack sufficient voice and messaging fraud protection as AI-powered vishing and smishing skyrocket following the launch of ChatGPT, according to Enea. 61% of enterprises still suffer significant losses to mobile fraud, with smishing and vishing being the most prevalent and costly.

Once the malicious software is installed, it redirects incoming calls to a call center under the control of the criminals. To facilitate the routing of voice traffic, "Letscall" utilizes cutting-edge technologies such as voice over IP and WebRTC. It also makes use of Session Traversal Utilities for NAT and Traversal Using Relays around NAT protocols, including Google STUN servers, to ensure high-quality phone or video calls and bypass NAT and firewall restrictions.

An Android voice phishing malware campaign known as FakeCalls has reared its head once again to target South Korean users under the guise of over 20 popular financial apps. FakeCalls was previously documented by Kaspersky in April 2022, describing the malware's capabilities to imitate phone conversations with a bank customer support agent.