Security News

Ukraine's cyberpolice has arrested members of a fraud gang that stole roughly $4,300,000 from over a thousand victims across the EU. The crime group created over 100 fake "Phishing" sites targeting users in France, Spain, Poland, the Czech Republic, Portugal, and other European countries, enticing them with products below market prices. Orders placed by the victims didn't correspond to actual purchases, while the threat actors stole credit card details they entered on the phony sites.

The Computer Emergency Response Team of Ukraine has issued an alert warning of cyber attacks against state authorities in the country that deploy a legitimate remote access software named Remcos. The bogus emails that kick-start the infection sequence claim to be from Ukrainian telecom company Ukrtelecom and come bearing a decoy RAR archive.
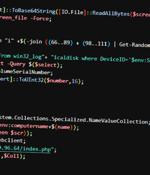
The State Cyber Protection Centre of Ukraine has called out the Russian state-sponsored threat actor known as Gamaredon for its targeted cyber attacks on public authorities and critical information infrastructure in the country. All the analyzed VBScript droppers and PowerShell scripts, per SCPC, are variants of GammaLoad and GammaSteel malware, respectively, effectively permitting the adversary to exfiltrate sensitive information.

ESET researchers have discovered yet another wiper malware used to target Ukrainian organizations. Dubbed SwiftSlicer, it is thought to be wielded by the Sandworm APT. Simultaneously, the Ukranian CERT has confirmed that the attackers who recently aimed to disrupting the operation of the National News Agency of Ukraine used various wiper malware and one legitimate Windows command line utility to try to "Destroy" machines running different operating systems.

Government entities in Ukraine have been breached as part of a new campaign that leveraged trojanized versions of Windows 10 installer files to conduct post-exploitation activities. Mandiant, which discovered the supply chain attack around mid-July 2022, said the malicious ISO files were distributed via Ukrainian- and Russian-language Torrent websites.

Ukrainian government entities were hacked in targeted attacks after their networks were first compromised via trojanized ISO files posing as legitimate Windows 10 installers. While analyzing several infected devices on Ukrainian Government networks, Mandiant also spotted scheduled tasks set up in mid-July 2022 and designed to receive commands that would get executed via PowerShell.

The China-linked nation-state hacking group referred to as Mustang Panda is using lures related to the ongoing Russo-Ukrainian War to attack entities in Europe and the Asia Pacific. Mustang Panda is a prolific cyber-espionage group from China that's also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.
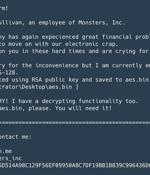
Ukraine has come under a fresh onslaught of ransomware attacks that mirror previous intrusions attributed to the Russia-based Sandworm nation-state group. Slovak cybersecurity company ESET, which dubbed the new ransomware strain RansomBoggs, said the attacks against several Ukrainian entities were first detected on November 21, 2022.

The Ukrainian CERT has uncovered an attack campaign aimed at compromising Ukrainian organizations and irretrievably encrypting their files. To do that, they are leveraging a specific version of the Somnia ransomware that, "According to the attackers' theoretical plan, does not provide for the possibility of data decryption."

Separately, charges slapped on alleged operator of dark market, The Real Deal Mark Sokolovsky, 26, a Ukrainian national, is being held in the Netherlands while he awaits extradition to America on...