Security News
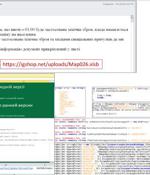
The Computer Emergency Response Team of Ukraine has warned of phishing attacks that deploy an information-stealing malware called Jester Stealer on compromised systems. The mass email campaign carries the subject line "Chemical attack" and contains a link to a macro-enabled Microsoft Excel file, opening which leads to computers getting infected with Jester Stealer.

The Computer Emergency Response Team of Ukraine has warned of a new wave of social engineering campaigns delivering IcedID malware and leveraging Zimbra exploits with the goal of stealing sensitive information. Attributing the IcedID phishing attacks to a threat cluster named UAC-0041, the agency said the infection sequence begins with an email containing a Microsoft Excel document that, when opened, prompts the users to enable macros, leading to the deployment of IcedID. The information-stealing malware, also known as BokBot, has followed a similar trajectory to that of TrickBot, Emotet, and ZLoader, evolving from its earlier roots as a banking trojan to a full-fledged crimeware service that facilities the retrieval of next-stage implants such as ransomware.

Hackers are targeting Ukrainian government agencies with new attacks exploiting Zimbra exploits and phishing attacks pushing the IcedID malware. The Computer Emergency Response Team of Ukraine detected the new campaigns and attributed the IcedID phishing attack to the UAC-0041 threat cluster, previously connected with AgentTesla distribution, and the second to UAC-0097, a currently unknown actor.

A Russian cyberweapon, similar to the one used in 2016, was detected and removed before it could be used. ESET researchers collaborated with CERT-UA to analyze the attack against the Ukrainian energy company The destructive actions were scheduled for 2022-04-08 but artifacts suggest that the attack had been planned for at least two weeks The attack used ICS-capable malware and regular disk wipers for Windows, Linux and Solaris operating systems We assess with high confidence that the attackers used a new version of the Industroyer malware, which was used in 2016 to cut power in Ukraine We assess with high confidence that the APT group Sandworm is responsible for this new attack Posted on April 13, 2022 at 6:32 AM 0 Comments.

The Russian state-sponsored hacking group known as Sandworm tried on Friday to take down a large Ukrainian energy provider by disconnecting its electrical substations with a new variant of the Industroyer malware for industrial control systems and a new version of the CaddyWiper data destruction malware. The threat actor used a version of the Industroyer ICS malware customized for the target high-voltage electrical substations and then tried to erase the traces of the attack by executing CaddyWiper and other data-wiping malware families tracked as Orcshred, Soloshred, and Awfulshred for Linux and Solaris systems.

A 32-year-old Ukrainian national has been sentenced to five years in prison in the U.S. for the individual's criminal work as a "High-level hacker" in the financially motivated group FIN7. FIN7 has been attributed to a number of attacks that have led to the theft of more than 20 million customer card records from over 6,500 individual point-of-sale terminals at more than 3,600 separate business locations in the U.S, costing the victims $1 billion in losses.

Hackers are compromising WordPress sites to insert a malicious script that uses visitors' browsers to perform distributed denial-of-service attacks on Ukrainian websites. Today, MalwareHunterTeam discovered a WordPress site compromised to use this script, targeting ten websites with Distributed Denial of Service attacks.

Facebook has removed a deepfake video of Ukrainian President Volodymyr Zelenskyy spreading across the social network and the Internet, asking Ukrainian troops lay down their arms and surrender. "Earlier today, our teams identified and removed a deepfake video claiming to show President Zelensky issuing a statement he never did," said Nathaniel Gleicher, the head of security policy at Meta, Facebook's parent company.

Today, Chris Evans, the CISO of bug bounty platform HackerOne, apologized to Ukrainian hackers after erroneously blocking their bug bounty payouts following sanctions imposed on Russia and Belarus after Ukraine's invasion. "Due to current economic sanctions and export controls, if you are based in Ukraine, Russia, or Belarus all communications and transactions have been paused for the time being," an email received by Ukrainian hackers from HackerOne read. The decision to freeze accounts for Ukrainians on the bug bounty platforms was also shared by HackerOne CEO Mårten Mickos via a now-deleted tweet saying that the company would re-route all rewards to UNICEF for all hackers from sanctioned areas.
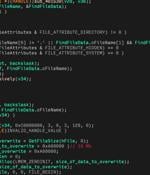
Two weeks after details emerged about a second data wiper strain delivered in attacks against Ukraine, yet another destructive malware has been detected amid Russia's continuing military invasion of the country. Slovak cybersecurity company ESET dubbed the third wiper "CaddyWiper," which it said it first observed on March 14 around 9:38 a.m. UTC. Metadata associated with the executable shows that the malware was compiled at 7:19 a.m. UTC, a little over two hours prior to its deployment.