Security News

Users in Brazil are the target of a new banking trojan known as CHAVECLOAK that's propagated via phishing emails bearing PDF attachments. "This intricate attack involves the PDF downloading a ZIP...

An "intricately designed" remote access trojan (RAT) called Xeno RAT has been made available on GitHub, making it available to other actors at no extra cost. Written in C# and compatible with...
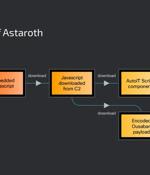
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka...

Security researchers are warning of hackers abusing the Google Cloud Run service to distribute massive volumes of banking trojans like Astaroth, Mekotio, and Ousaban. Google Cloud Run is lets users deploy frontend and backend services, websites or applications, handle workloads without the effort of managing an infrastructure or scaling.

The Android banking trojan known as Anatsa has expanded its focus to include Slovakia, Slovenia, and Czechia as part of a new campaign observed in November 2023. "Some of the droppers in the...

Group-IB uncovered a new iOS trojan designed to steal users' facial recognition data, identity documents, and intercept SMS. The trojan, dubbed GoldPickaxe. iOS trojan targets victims in the Asia-Pacific region.

Sixty-one banking institutions, all of them originating from Brazil, are the target of a new banking trojan called Coyote. "This malware utilizes the Squirrel installer for distribution,...

The threat actors behind the Mispadu banking Trojan have become the latest to exploit a now-patched Windows SmartScreen security bypass flaw to compromise users in Mexico. The attacks entail a new...

A Brazilian law enforcement operation has led to the arrest of several Brazilian operators in charge of the Grandoreiro malware. The Federal Police of Brazil said it served five temporary arrest...

A malicious package uploaded to the npm registry has been found deploying a sophisticated remote access trojan on compromised Windows machines. The package, named "oscompatible," was published on...