Security News

Dubbed ChaChi by researchers at BlackBerry, the RAT has recently shifted its focus from government agencies to schools in the US. A Remote Access Trojan is targeting schools and universities with ransomware attacks. Specifically, ChaChi has been discovered in data breaches of K-12 schools and higher education facilities in the U.S. as well as the U.K. SEE: Special report: A winning strategy for cybersecurity.

Bizarro is a new banking trojan that is stealing financial information and crypto wallets. The program can be delivered in a couple of ways - either via malicious links contained within spam emails, or through a trojanized app.

A never-before-documented Brazilian banking trojan, dubbed Bizarro, is targeting customers of 70 banks scattered throughout Europe and South America, researchers said. Once installed, it kills all running browser processes to terminate any existing sessions with online banking websites - so, when a user initiates a mobile banking session, they have to sign back in, allowing the malware to harvest the details.

Researchers have discovered an Android trojan that can steal victims' SMS messages and credentials and completely take over devices. Once installed on a victim's device, attackers can use the trojan to obtain a live streaming of the device screen on demand and also interact with it via Accessibility Services, according to a report posted online by online fraud-management firm Cleafy about the trojan, which is also tracked by the name "Anatsa."

Cybersecurity researchers on Monday disclosed a new Android trojan that hijacks users' credentials and SMS messages to facilitate fraudulent activities against banks in Spain, Germany, Italy, Belgium, and the Netherlands. Called "TeaBot", the malware is said to be in its early stages of development, with malicious attacks targeting financial apps commencing in late March 2021, followed by a rash of infections in the first week of May against Belgium and Netherlands banks.

Ten variants of the Joker Android Trojan managed to slip into the Huawei AppGallery app store and were downloaded by more than 538,000 users, according to new data from Russian anti-malware vendor Doctor Web. Also known as Bread, the Joker Trojan was first observed in 2017 when it was originally focused on SMS fraud.

The threat actors behind the IcedID Trojan are experimenting with various delivery methods to increase efficiency, including sending malicious messages from web-based contact forms. Some of the attacks switched to the abuse of contact forms for the delivery of malicious messages.

The banking trojan known as IcedID appears to be taking the place of the recently disrupted Emotet trojan, according to researchers. IcedID, bears similarities to Emotet in that it's a modular malware that started life as a banking trojan used to steal financial information.
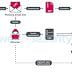
Researchers on Tuesday revealed details of a new banking trojan targeting corporate users in Brazil at least since 2019 across various sectors such as engineering, healthcare, retail, manufacturing, finance, transportation, and government. "These pop-ups contain fake forms, aiming to trick the malware's victims into entering their banking credentials and personal information that the malware captures and exfiltrates to its servers," ESET researchers Facundo Muñoz and Matías Porolli said in a write-up.

Enterprise software developer Proxmox Server Solutions GmbH has released Proxmox Mail Gateway 6.4, the latest version of its open-source email security solution. Proxmox Mail Gateway is a complete operating system based on Debian Buster 10.9, but using Linux kernel 5.4.106, which is under long term support status.