Security News

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft patches two zero-days exploited in the wild (CVE-2024-43573, CVE-2024-43572) For October...

Russian government agencies and industrial entities are the target of an ongoing activity cluster dubbed Awaken Likho. "The attackers now prefer using the agent for the legitimate MeshCentral...

Security operations center (SOC) practitioners believe they are losing the battle detecting and prioritizing real threats – due to too many siloed tools and a lack of accurate attack signal,...

Rigid security protocols — such as complex authentication processes and highly restrictive access controls — can frustrate employees, slow productivity and lead to unsafe workarounds, according to...

Dynamic malware analysis is a key part of any threat investigation. It involves executing a sample of a malicious program in the isolated environment of a malware sandbox to monitor its behavior...
A new set of malicious packages has been unearthed in the Python Package Index (PyPI) repository that masqueraded as cryptocurrency wallet recovery and management services, only to siphon...

In this Help Net Security interview, Raymond Brancato, CEO at Tufin, discusses the considerations organizations must weigh when selecting a next-generation firewall to effectively balance security...

Here are the top cyber threat hunting tools that can enhance your organization's cybersecurity defenses. Learn how their features compare.
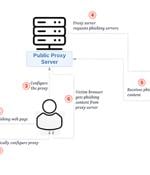
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past year, indicating that it's being used by a large number of...

Organizations are combating excessive remote access demands with an equally excessive number of tools that provide varying degrees of security, according to Claroty. Data from more than 50,000...