Security News

Leveraging threat intelligence to tackle supply chain vulnerabilitiesIn this interview with Help Net Security, Brandon Hoffman, CISO at Intel 471, talks about the growing threat of supply chain attacks, the most common supply chain vulnerabilities and how the right threat intelligence can help stay on top of these threats. 3 ways any company can guard against insider threats this OctoberOctober is Cybersecurity Awareness Month, but most business leaders and consumers don't need a special event to remember cybersecurity's preeminence in today's turbulent digital landscape.
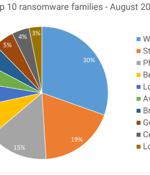
Move over REvil, Ragnar Locker, BlackMatter, Conti et al: Three lesser-known gangs account for the vast majority of ransomware attacks in the U.S. and globally. While there seem to be legions of ransomware gangs, it turns out that just a handful of ransomware-as-a-service actors dominate the entire ecosystem of encryption-attack threats.

Security specialist ESET's latest Threat Report warns of a massive increase in attacks on Remote Desktop Protocol endpoints - and new activity from the Nobelium gang against European government organisations. ESET's figures show attacks on RDP servers having gone up 103.9 per cent since its T1 report in June - it publishes three a year - representing a total of 55 billion detected brute-force attacks, thanks in no small part to a campaign focused on Spanish targets.
While organizations recognize third-party threats expose them to great risk, many organizations fail to take adequate measures to mitigate it. Current third-party risk prevention strategies leave organizations vulnerable.

Private sector remaining skeptical about govt's ability to mitigate cyber threats. Despite recent interventions into cybersecurity issues, executives lack faith in the government's ability to protect them from cyber threats, with 60% of organizations believing that spending on new security tools and services is the most effective way of stopping attacks.

The US Cybersecurity and Infrastructure Security Agency has released a new tool that allows public and private sector organizations to assess their vulnerability to insider threats and devise their own defense plans against such risks. The Insider Risk Mitigation Self-Assessment Tool helps orgs determine their risk posture by answering a series of questions about the requirements needed to set up an insider risk program management, the levels of insider risk awareness and training among employees, and the organization's insider risk environment.

Cybercriminals are using Telegram bots to steal one-time password tokens and defraud people through banks and online payment systems, including PayPal, Apple Pay and Google Pay, new research has found. Threat actors are using Telegram bots and channels and a range of tactics to gain account information, including calling victims, and impersonating banks and legitimate services, researchers said.

In this interview with Help Net Security, Brandon Hoffman, CISO at Intel 471, talks about the growing threat of supply chain attacks, the most common supply chain vulnerabilities and how the right threat intelligence can help stay on top of these threats. We are witnessing a growing number of supply chain attacks lately, and cybercriminals are becoming stealthier and smarter.

October is Cybersecurity Awareness Month, but most business leaders and consumers don't need a special event to remember cybersecurity's preeminence in today's turbulent digital landscape. While software solutions are critical to securing digital infrastructure and company data, businesses will get the most return-on-investment by directing a significant share of their cybersecurity capacity toward an oft-overlooked priority - their people.

Attackers can easily buy, deploy and scale phishing campaigns to steal credentials and other sensitive data, says Microsoft. Cybercrime as a service has expanded to malware, ransomware and even phishing campaigns.