Security News

This overlooked vulnerability is no trivial matter, and it raises the critical question: Are we doing enough to insulate our code and applications from the risks of prompt injection? Prompt injection is an insidious technique where attackers introduce malicious commands into the free text input that controls an LLM. By doing so, they can force the model into performing unintended and malicious actions.

While many IT workers see the productivity benefits of AI, 56% believe it benefits employers more than employees, according to Ivanti. 63% are concerned generative AI tools might take their job in the next five years compared to 44% of office workers.

Security teams need easily replicable techniques to emulate threat scenarios to test their defense skills against the skill level of cyber-attackers. At least yearly, there should be a full red team assessment; the red team is made up of offensive security professionals whose role is to exploit the company's vulnerabilities and overcome cybersecurity controls.
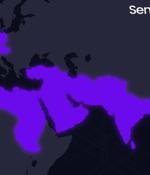
A previously undocumented threat actor dubbed Sandman has been attributed to a set of cyber attacks targeting telecommunic koation providers in the Middle East, Western Europe, and the South Asian...

The financially motivated threat actor known as UNC3944 is pivoting to ransomware deployment as part of an expansion to its monetization strategies, Mandiant has revealed. "UNC3944 has demonstrated a stronger focus on stealing large amounts of sensitive data for extortion purposes and they appear to understand Western business practices, possibly due to the geographical composition of the group," the threat intelligence firm said.

Proactive threat intelligence was not automated threat intelligence, however. Automated threat intelligence helped teams operate more efficiently, but it presented a novel challenge: How to manage and make sense of all the data that automated threat intelligence processes produced.
As organizations integrate more SaaS applications into their workflows, they inadvertently open the door to a new era of security threats. Historically, SaaS security was about managing misconfigurations.

Deepfake videos use AI and deep learning techniques to create highly realistic but fake or fabricated content. The most effective evaluation of deepfake technology can be made when watching videos in which the "Deepfaked" person is a celebrity or individual whom the viewer is visually familiar with.

85% of phishing emails utilized malicious links in the content of the email, and spam emails increased by 30% from Q1 to Q2 2023, according to a VIPRE report. Information technology organizations also overtook financial institutions as the most targeted sector for phishing in Q2 as compared to VIPRE's previous quarterly report.
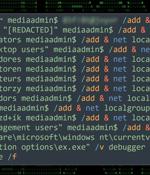
Threat actors are exploiting poorly secured Microsoft SQL servers to deliver Cobalt Strike and a ransomware strain called FreeWorld. "The ransomware payload of choice appears to be a newer variant of Mimic ransomware called FreeWorld."