Security News

Cybersecurity is an overly reactive industry. Too often we act like firefighters, rushing from blaze to blaze, extinguishing flames hoping to keep the damage to a minimum, rather than fire...

Malvertising is a shortened mash-up of “malicious advertising.” In a nutshell, malvertising is a relatively new cyberattack method in which bad actors inject malicious code into digital ads. These...

The U.S. government (USG) has issued new guidance governing the use of the Traffic Light Protocol (TLP) to handle the threat intelligence information shared between the private sector, individual...

Cybersecurity news can sometimes feel like a never-ending horror movie, can't it? Just when you think the villains are locked up, a new threat emerges from the shadows. This week is no exception,...
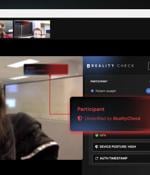
Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to a potent weapon in the hands of bad actors. Today, AI-based attacks are not just theoretical threats—they're happening...

It only takes five days on average for attackers to exploit a vulnerability, according to a new report.

Recently, IBM X-Force released its 2024 Cloud Threat Landscape Report. This uses incident data and insights to reveal how attackers successfully compromise organizations by leveraging...

Hi there! Here’s your quick update on the latest in cybersecurity. Hackers are using new tricks to break into systems we thought were secure—like finding hidden doors in locked houses. But the...

The German car giant appears to be unconcerned The 8Base ransomware crew claims to have stolen a huge data dump of Volkswagen files and is threatening to publish them, but the German car giant...
