Security News

There's no alert about the bug visible on the company's main web page, which features the company's best-known tools JIRA and Trello, but you'll find Confluence Security Advisory 2022-06-02 on the Confluence sub-site. Webshells are a nasty way of opening up a backdoor into a network using an attack that sometimes requires attackers to do little more than write one tiny file into part of a web server where content is stored.

Virtual Private Network provider ExpressVPN on Thursday announced that it's removing Indian-based VPN servers in response to a new cybersecurity directive issued by the Indian Computer Emergency Response Team. "Rest assured, our users will still be able to connect to VPN servers that will give them Indian IP addresses and allow them to access the internet as if they were located in India," the company said.

Virtual private network operator ExpressVPN will pull its servers from India, citing the impossibility of complying with the nation's incoming requirement to record users' identities and activities. ExpressVPN offers software that routes traffic through servers that load their operating systems entirely into RAM and therefore leave no trace of users' activities on persistent media.
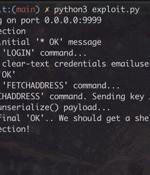
A new unpatched security vulnerability has been disclosed in the open-source Horde Webmail client that could be exploited to achieve remote code execution on the email server simply by sending a specially crafted email to a victim. "Once the email is viewed, the attacker can silently take over the complete mail server without any further user interaction," SonarSource said in a report shared with The Hacker News.
"Now it is significantly harder to separate the wheat from the chaff and discover the real C&C servers among thousands of legitimate domains used by Xloader as a smokescreen," Israeli cybersecurity company Check Point said. The latest findings from Check Point build on a previous report from Zscaler in January 2022, which revealed the inner workings of the malware's C&C network encryption and communication protocol, noting its use of decoy servers to conceal the legitimate server and evade malware analysis systems.

Over 3.6 million MySQL servers are publicly exposed on the Internet and responding to queries, making them an attractive target to hackers and extortionists. Of these accessible MySQL servers, 2.3 million are connected over IPv4, with 1.3 million devices over IPv6.

Threat analysts have spotted a new version of the XLoader botnet malware that uses probability theory to hide its command and control servers, making it difficult to disrupt the malware's operation. XLoader already camouflaged its actual command and control servers in version 2.3 by hiding the real domain name in a configuration that includes 63 decoys.

A rapidly evolving IoT malware dubbed "EnemyBot" is targeting content management systems, web servers and Android devices. The Alien lab research team study found four main sections of the malware.
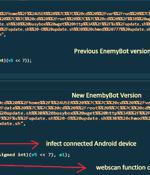
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems. "The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week.

"An attacker running code on a vulnerable QCT server would be able to 'hop' from the server host to the BMC and move their attacks to the server management network, possibly continue and obtain further permissions to other BMCs on the network and by doing that gaining access to other servers," firmware and hardware security firm Eclypsium said. A baseboard management controller is a specialized system used for remote monitoring and management of servers, including controlling low-level hardware settings as well as installing firmware and software updates.