Security News

ALSO: Viasat hack wiper malware is back, users are the number one cause of data loss, and critical vulns Infosec in brief If your Windows domain controllers have been crashing since a security...

Microsoft has released emergency out-of-band updates to fix a known issue causing Windows domain controllers to crash after installing the March 2024 Windows Server security updates. If you installed previous Windows Server updates, only the new updates in these packages will be downloaded and installed.

Microsoft confirmed that a memory leak introduced with the March 2024 Windows Server security updates is behind a widespread issue causing Windows domain controllers to crash. The known issue impacts all domain controller servers with the latest Windows Server 2012 R2, 2016, 2019, and 2022 updates.

A Syslog server will only collect messages in the Syslog format but it is possible to change other formats into the Syslog layout before sending them to a Syslog server; this is called "Conversion." The other option is to set up a non-specific TFTP server and implement format conversion through a post-receipt process; this is called "Consolidation." If you don't convert either before or after the transfer, you will be storing raw log messages. If you receive log messages through a Syslog server, they will be written either to files or to a database in the Syslog format.

The March 2024 Windows Server updates are causing some domain controllers to crash and restart, according to widespread reports from Windows administrators. Affected servers are freezing and rebooting because of a Local Security Authority Subsystem Service process memory leak introduced with the March 2024 cumulative updates for Windows Server 2016 and Windows Server 2022.

Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to...
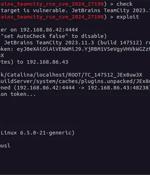
A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems. The flaws,...

The ALPHV/BlackCat ransomware gang has shut down its servers amid claims that they scammed the affiliate responsible for the attack on Optum, the operator of the Change Healthcare platform, of $22 million. Today, BleepingComputer confirmed the ransomware operations negotiation sites are now shut down as well, indicating a further deliberate take down of the ransomware gang's infrastructure.

The Main Intelligence Directorate of Ukraine's Ministry of Defense claims that it breached the servers of the Russian Ministry of Defense and stole sensitive documents. Software used by the Russian Ministry of Defense for protecting and encrypting data.

The LockBit ransomware gang is once again conducting attacks, using updated encryptors with ransom notes linking to new servers after last week's law enforcement disruption. Last week, the NCA, FBI, and Europol conducted a coordinated disruption called 'Operation Cronos' against the LockBit ransomware operation.