Security News

It's the classic battle fought over every app: UX designers hate security measures because they feel these measures inject complexity and make it harder for users to get what they want. Security teams feel like UX teams design for streamlined workflows and familiar processes at the cost of better security.

Despite stringent regulations and calls for 'security by design', organizations are still failing to equip teams with the knowledge to secure code, according to Security Journey. The survey reveals a reactive approach when it comes to security education programs, with 68% of respondents only undertaking secure coding training because of a compliance need or in response to an exploit.

To manage an environment of increasing risks and limited resources, healthcare internal audit and compliance departments must align their risk assessments and audit work plans to areas most vital to achieving the strategic goals and business objectives of their organizations, according to Kodiak. To unlock these benefits, healthcare provider organizations need to mitigate a host of risks, such as storing and securing enormous amounts of data that is mostly protected health information, protecting the training data for AI models from malicious actors seeking to introduce bad data, and rooting out bias that can creep into in AI algorithms because of a lack of data for gender, sexual orientation, race and ethnicity.

In today's digital world, security risks are more prevalent than ever, especially when it comes to Software as a Service (SaaS) applications. Did you know that an alarming 97% of companies face...

The increasing complexity of networks also brings forth heightened security challenges. Robust network security measures are essential to safeguard against cyber threats, ensuring the integrity, confidentiality, and availability of sensitive information.

Jack Cable, a CISA senior technical advisor, writes that in 2019 when he was a computer science student at Stanford University in California, he didn't need to take any cybersecurity courses to graduate. Nearly five years later, "That list of the top 24 universities in computer science hasn't changed: 23 still don't require cybersecurity," Cable wrote in his memo.

Hewlett Packard Enterprise disclosed today that suspected Russian hackers known as Midnight Blizzard gained access to the company's Microsoft Office 365 email environment to steal data from its cybersecurity team and other departments. In a new Form 8-K SEC filing, HPE says they were notified on December 12th that the suspected Russian hackers breached their cloud-based email environment in May 2023.

The U.K.'s National Cyber Security Centre has released a new study that finds generative AI may increase risks from cyber threats such as ransomware. The report sorted threats by potential for "Uplift" from generative AI and by the types of threat actors: nation-state sponsored, well-organized and less-skilled or opportunistic attackers.
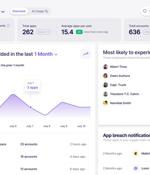
In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting new cloud and SaaS technologies whenever and wherever they need. While this has been a...

The ransomware group known as Kasseika has become the latest to leverage the Bring Your Own Vulnerable Driver (BYOVD) attack to disarm security-related processes on compromised Windows hosts,...