Security News

Microsoft says North Korean hacking groups have breached multiple Russian government and defense targets since the start of the year. "Multiple North Korean threat actors have recently targeted the Russian government and defense industry - likely for intelligence collection - while simultaneously providing material support for Russia in its war on Ukraine," said Clint Watts, the head of Microsoft's Digital Threat Analysis Center.

The power of the EU's Digital Services Act to actually police the world's very large online platforms has been tested in a new study focused on Russian social media disinformation. The independent study of the DSA's risk management framework published by the EU's executive arm, the European Commission, concluded that commitments by social media platforms to mitigate the reach and influence of global online disinformation campaigns have been generally unsuccessful.

Cybersecurity and intelligence agencies from Australia, Canada, New Zealand, the U.K., and the U.S. on Thursday disclosed details of a mobile malware strain targeting Android devices used by the Ukrainian military. The malicious software, dubbed Infamous Chisel and attributed to a Russian state-sponsored actor called Sandworm, has capabilities to "Enable unauthorized access to compromised devices, scan files, monitor traffic, and periodically steal sensitive information."
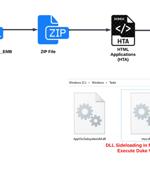
The phishing attacks feature PDF documents with diplomatic lures, some of which are disguised as coming from Germany, to deliver a variant of a malware called Duke, which has been attributed to APT29. "The threat actor used Zulip - an open-source chat application - for command-and-control, to evade and hide its activities behind legitimate web traffic," Dutch cybersecurity company EclecticIQ said in an analysis last week.

North Korean state-sponsored hackers have breached Russian missile maker NPO Mashinostroyeniya, according to SentinelLabs researchers. The researchers came across leaked email communication between NPO Mashinostroyeniya's IT staff that contained information about a possible cyber intrusion first detected in May 2022.

Two North Korean hacker groups had access to the internal systems of Russian missile and satellite developer NPO Mashinostoyeniya for five to six months, cyber security firm SentinelOne asserted on Monday. The attack illustrates potential North Korean efforts to advance development of missile and other military tech via cyber espionage.

The North Korean state-sponsored hacking group ScarCruft has been linked to a cyberattack on the IT infrastructure and email server for NPO Mashinostroyeniya, a Russian space rocket designer and intercontinental ballistic missile engineering organization. Today, SentinelLabs reported that ScarCruft is behind a hack of NPO Mashinostroyeniya's email server and IT systems, where the threat actors planted a Windows backdoor named 'OpenCarrot' for remote access to the network.

Two different North Korean nation-state actors have been linked to a cyber intrusion against the major Russian missile engineering company NPO Mashinostroyeniya. Cybersecurity firm SentinelOne said it identified "Two instances of North Korea related compromise of sensitive internal IT infrastructure," including a case of an email server compromise and the deployment of a Windows backdoor dubbed OpenCarrot.

An APT group linked to Russia’s Foreign Intelligence Service has hit employees of several dozen global organizations with phishing attacks via Microsoft Teams, says Microsoft. A social engineering...

Microsoft on Wednesday disclosed that it identified a set of highly targeted social engineering attacks mounted by a Russian nation-state threat actor using credential theft phishing lures sent as Microsoft Teams chats. Microsoft said the campaign, observed since at least late May 2023, affected less than 40 organizations globally spanning government, non-government organizations, IT services, technology, discrete manufacturing, and media sectors.