Security News

Cybersecurity researchers have disclosed 46 new security flaws in products from three solar power system vendors, Sungrow, Growatt, and SMA, that could be exploited by a bad actor to seize control...

A new investigation has unearthed nearly 200 unique command-and-control (C2) domains associated with a malware called Raspberry Robin. "Raspberry Robin (also known as Roshtyak or Storm-0856) is a...

Maddening techno loop, Zoolander reference, and 14 minutes of time wasted A vulnerability analyst and prominent member of the infosec industry has blasted Microsoft for refusing to look at a bug...

Google paid almost $12 million in bug bounty rewards to 660 security researchers who reported security bugs through the company's Vulnerability Reward Program (VRP) in 2024. [...]
Cybersecurity researchers have demonstrated a novel technique that allows a malicious web browser extension to impersonate any installed add-on. "The polymorphic extensions create a pixel perfect...

Threat actors deploying the Black Basta and CACTUS ransomware families have been found to rely on the same BackConnect (BC) module for maintaining persistent control over infected hosts, a sign...

PLUS: DOGE web design disappoints; FBI stops crypto scams; Zacks attacked again; and more! Infosec In Brief A security researcher has found that Google could leak the email addresses of YouTube...
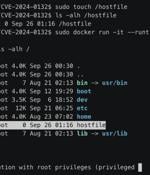
Cybersecurity researchers have discovered a bypass for a now-patched security vulnerability in the NVIDIA Container Toolkit that could be exploited to break out of a container's isolation...

Cybersecurity researchers have found that the Microsoft Active Directory Group Policy that's designed to disable NT LAN Manager (NTLM) v1 can be trivially bypassed by a misconfiguration. "A simple...

Ivanti has rolled out security updates to address several security flaws impacting Avalanche, Application Control Engine, and Endpoint Manager (EPM), including four critical bugs that could lead...