Security News
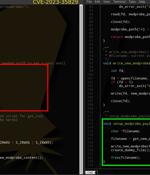
"In this instance, the PoC is a wolf in sheep's clothing, harboring malicious intent under the guise of a harmless learning tool," Uptycs researchers Nischay Hegde and Siddartha Malladi said. The repository masquerades as a PoC for CVE-2023-35829, a recently disclosed high-severity flaw in the Linux kernel.

OpenAI is seeking researchers to work on containing super-smart artificial intelligence with other AI. The end goal is to mitigate a threat of human-like machine intelligence that may or may not be science fiction. "We need scientific and technical breakthroughs to steer and control AI systems much smarter than us," wrote OpenAI Head of Alignment Jan Leike and co-founder and Chief Scientist Ilya Sutskever in a blog post.

Details have emerged about a newly identified security flaw in the Linux kernel that could allow a user to gain elevated privileges on a target host. Dubbed StackRot, the flaw impacts Linux versions 6.1 through 6.4.

In what's an ingenious side-channel attack, a group of academics has found that it's possible to recover secret keys from a device by analyzing video footage of its power LED. "Cryptographic computations performed by the CPU change the power consumption of the device which affects the brightness of the device's power LED," researchers from the Ben-Gurion University of the Negev and Cornell University said in a study. "This is caused by the fact that the power LED is connected directly to the power line of the electrical circuit which lacks effective means of decoupling the correlation with the power consumption," the researchers said.

Millions of GitHub repositories may be vulnerable to dependency repository hijacking, also known as "RepoJacking," which could help attackers deploy supply chain attacks impacting a large number of users. The warning comes from AquaSec's security team, 'Nautilus,' who analyzed a sample of 1.25 million GitHub repositories and found that about 2.95% of them to be vulnerable to RepoJacking.

Three security vulnerabilities have been disclosed in operational technology products from Wago and Schneider Electric. The flaws, per Forescout, are part of a broader set of shortcomings collectively called OT:ICEFALL, which now comprises a total of 61 issues spanning 13 different vendors.

Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems. On devices running macOS, Base64-encoded content retrieved from the server is written to a file named "/Users/Shared/AppleAccount.

At least half of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity company have been observed pushing malicious repositories on the code hosting service. VulnCheck, which discovered the activity, said, "The individuals creating these repositories have put significant effort into making them look legitimate by creating a network of accounts and Twitter profiles, pretending to be part of a non-existent company called High Sierra Cyber Security."
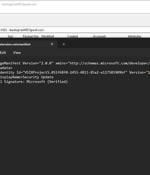
Security researchers have warned about an "Easily exploitable" flaw in the Microsoft Visual Studio installer that could be abused by a malicious actor to impersonate a legitimate publisher and distribute malicious extensions. "A threat actor could impersonate a popular publisher and issue a malicious extension to compromise a targeted system," Varonis researcher Dolev Taler said.

The number of stolen Asian credit card numbers appearing on darkweb crime marts has fallen sharply, cyber security firm Group-IB told Singapore's ATxSG conference on Thursday. Out of 29 million compromised accounts found on sale on the dark web, over 12 million featured top level domains related to India.