Security News

A recent study by Wing Security found that 63% of businesses may have former employees with access to organizational data, and that automating SaaS Security can help mitigate offboarding risks. ...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

With this map, the researchers can explore how neuron-like data points, called features, affect a generative AI's output. Some of these features are "Safety relevant," meaning that if people reliably identify those features, it could help tune generative AI to avoid potentially dangerous topics or actions.

A new report from XM Cyber has found – among other insights - a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The...
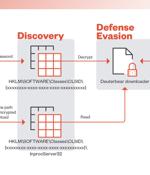
Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for...

The Mobile Security Framework is an open-source research platform for mobile application security, encompassing Android, iOS, and Windows Mobile. MobSF can be used for mobile app security assessment, penetration testing, malware analysis, and privacy evaluation.

Most cybersecurity professionals believe AI will significantly impact their jobs, according to a new survey by the International Information System Security Certification Consortium; with only 35% of the respondents having already witnessed AI's effects on their jobs. The impact is not necessarily a positive or negative impact, but rather an indicator that cybersecurity pros expect their jobs to change.

With many of the highly publicized 2023 cyber attacks revolving around one or more SaaS applications, SaaS has become a cause for genuine concern in many boardroom discussions. More so than ever,...

Google is currently tracking more than 40 CSVs, most of which are highly technical with the ability to develop spyware and zero-day exploits to compromise their targets, particularly on Android and iOS devices. Read details about what CSVs target, how spyware is used, CSVs' harmful impact on individuals and society and how businesses can mitigate these cybersecurity threats.

The Main Intelligence Directorate of Ukraine's Ministry of Defense claims that pro-Ukrainian hacktivists breached the Russian Center for Space Hydrometeorology, aka "Planeta", and wiped 2 petabytes of data. Planeta is a state research center using space satellite data and ground sources like radars and stations to provide information and accurate predictions about weather, climate, natural disasters, extreme phenomena, and volcanic monitoring.