Security News

A new State of SaaS Security Posture Management Report from SaaS cybersecurity provider AppOmni indicates that Cybersecurity, IT, and business leaders alike recognize SaaS cybersecurity as an increasingly important part of the cyber threat landscape. When asked to rate the SaaS cybersecurity maturity level of their organizations, 71% noted that their organizations' SaaS cybersecurity maturity has achieved either a mid-high level or the highest level.

Phishing is so last year: Akamai's report finds that zero-day and one-day vulnerabilities caused a 143% increase in total ransomware victims. Akamai's ransomware report released at Black Hat 2023 revealed that exploitation of zero-day and one-day vulnerabilities has led to a 143% increase in total ransomware victims with data exfiltration of files at the end of the kill chain, now the primary source of extortion.

The just-released BlackBerry Global Threat Intelligence Report reveals a 40% increase in cyberattacks against government and public service organizations versus the previous quarter. With limited resources and often immature cyber defense programs, these publicly funded organizations are struggling against the double-pronged threat of attacks from both nation-states and the criminal underground.

Tactical similarities have been unearthed between the double extortion ransomware group known as Rhysida and Vice Society, including in their targeting of education and healthcare sectors. "As Vice Society was observed deploying a variety of commodity ransomware payloads, this link does not suggest that Rhysida is exclusively used by Vice Society, but shows with at least medium confidence that Vice Society operators are now using Rhysida ransomware," Check Point said in a new report.

I had no idea that squid contain sufficient oil to be worth extracting. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

Chinese companies, including state-owned defense companies, are evading tech sanctions and fueling Moscow's war in Ukraine, according to a US report released on Thursday. "Beijing is pursuing a variety of economic support mechanisms for Russia that mitigate both the impact of Western sanctions and export controls," states the report.

Data breach costs rose to $4.45 million per incident in 2023, IBM found in its annual Cost of a Data Breach report. Average data breach cost rose to $4.45 million per incident.

Microsoft is making it easier to see how much energy your apps use in Windows 11 over a given period by introducing a detailed power consumption page in the latest 23H2 update. The power consumption page provides a comprehensive report of energy use over the last 24 hours or the last seven days.

The Europol report also reported on cybercriminals' use of cryptocurrencies and how their techniques are more sophisticated. The Europol report reported on cybercriminals' use of cryptocurrencies and how their techniques are more sophisticated.
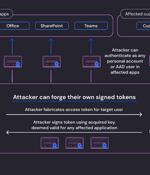
According to cloud security company Wiz, the inactive Microsoft account consumer signing key used to forge Azure Active Directory tokens to gain illicit access to Outlook Web Access and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications. Wiz's analysis fills in some of the blanks, with the company discovering that "All Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."