Security News

Cybercrime gangs like the notorious Lazarus group and spyware vendors like Israel's NSO should be considered cyber mercenaries - and become the subject of a concerted international response - according to a Monday report from Delhi-based think tank Observer Research Foundation. Author Fitri Bintang Timur argued the term mercenary applies because, as amendments to the Geneva Convention put it, mercenaries are "An entity having the motivation to gain financial or material compensation in return for their willingness to fight for the recruiter's country."

We'll focus on three topics covered: the ransomware cybercriminal ecosystem, network infrastructure attacks and commodity loader malware. More ransomware actors switched to extortion rather than encryption, while commodity loaders evolved to be stealthier and highly effective, although new major security improvements have seen the day in 2023, such as Microsoft Office disabling macros by default.

Compromising the browser is a high-return target for adversaries. Browser extensions, which are small software modules that are added to the browser and can enhance browsing experiences, have...

Please turn on your JavaScript for this page to function normally. This survey set out to explore these challenges, to identify common practices, and to provide insight into how organizations can bolster their defenses.

GitHub Advanced Security gains AI features, and GitHub Copilot now includes a chatbot option. At the GitHub Universe conference held in San Francisco and virtually on Nov. 8 and Nov. 9, 2023, the company revealed its new open source trends report as well as changes to GitHub Copilot and AI enhancements for GitHub Advanced Security.

The U.S. Federal Trade Commission has amended the Safeguards Rules, mandating that all non-banking financial institutions report data breach incidents within 30 days. "The addition of this disclosure requirement to the Safeguards Rule should provide companies with additional incentive to safeguard consumers' data."

TechRepublic Premium Hiring Kit: Cloud Engineer Regardless of what business or what industry you are in, the potential benefits of cloud computing and cloud computing services are self-evident. With so many businesses flooding .... TechRepublic Premium Hiring Kit: Data Architect To make their best decisions, businesses need the best actionable information.

A new report from Netskope detailing the top techniques used by cybercriminals to attack organizations found that cloud apps are increasingly being used by threat actors, representing 19% of all clicks on spearphishing links. Netskope recently reported that Microsoft OneDrive is the most popular cloud app used in enterprises, so it is not a surprise that attackers leverage this target a lot, alongside Microsoft Teams, SharePoint and Outlook.
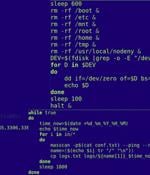
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that threat actors "interfered" with at least 11 telecommunication service providers in the country between May and September...

Encrypted messaging app Signal has pushed back against "viral reports" of an alleged zero-day flaw in its software, stating it found no evidence to support the claim. "After responsible...