Security News

Several ransomware actors are using a malware called Skitnet as part of their post-exploitation efforts to steal sensitive data and establish remote control over compromised hosts. "Skitnet has...
Universities and government organizations in North America and Asia have been targeted by a previously undocumented Linux malware called Auto-Color between November and December 2024, according to...

The North Korean hacking group known as Kimsuky was observed in recent attacks using a custom-built RDP Wrapper and proxy tools to directly access infected machines. [...]

Cybersecurity researchers have called attention to a software supply chain attack targeting the Go ecosystem that involves a malicious package capable of granting the adversary remote access to...

Cybersecurity researchers have disclosed details of a new BackConnect (BC) malware that has been developed by threat actors linked to the infamous QakBot loader. "BackConnect is a common feature...
A now-patched critical security flaw impacting Fortinet FortiClient EMS is being exploited by malicious actors as part of a cyber campaign that installed remote desktop software such as AnyDesk...

BeyondTrust has fixed an unauthenticated command injection vulnerability (CVE-2024-12356) in its Privileged Remote Access (PRA) and Remote Support (RS) products that may allow remote code...

This Remote Access Checklist, created by Scott Matteson for TechRepublic Premium, should be used to ensure all employees have the requisite items, accounts, access, and instructions needed for...

Chinese hackers targeting large IT service providers in Southern Europe were seen abusing Visual Studio Code (VSCode) tunnels to maintain persistent access to compromised systems. [...]
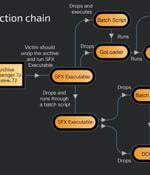
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to deliver DarkCrystal RAT (aka DCRat) and a previously...