Security News

Ivanti on Tuesday rolled out fixes to address multiple critical security flaws in Endpoint Manager (EPM) that could be exploited to achieve remote code execution under certain circumstances. Six...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
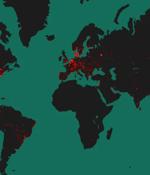
More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that's vulnerable to a critical unpatched security flaw in the HTTP/HTTPS proxy tool. The issue,...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Bitdefender researchers have uncovered four vulnerabilities in webOS, the operating system running on LG smart TVs, which may offer attackers unrestricted access to the devices. The number of potentially exploitable internet-connected devices is likely smaller, as LG has patched the vulnerabilities on March 22, 2023, and some of the users have either applied the updates or have set their TVs to perform updates automatically.

Security researchers at Bitdefender have discovered four vulnerabilities impacting multiple versions of WebOS, the operating system used in LG smart TVs. The flaws enable varying degrees of unauthorized access and control over affected models, including authorization bypasses, privilege escalation, and command injection. The potential attacks hinge on the ability to create arbitrary accounts on the device using a service that runs on ports 3000/3001, which is available for smartphone connectivity, using a PIN. Bitdefender explains that although the vulnerable LG WebOS service is supposed to be used only in local area networks settings, Shodan internet scans show 91,000 exposed devices that are potentially vulnerable to the flaws.

The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable of facilitating remote code execution, a new analysis...

The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection evasion techniques, enabling its operators to remotely interact with...

As corporate conglomerates, small businesses and brick-and-mortar shops fade away in favor of a distributed offsite workforce, companies and employees can profit from the greater convenience and efficiency provided by remote access. Combined with a bring your own device policy, remote access can lower equipment costs, reduce office overhead and facilitate employee productivity.

State-sponsored hackers affiliated with China have targeted small office/home office routers in the U.S. in a wide-ranging botnet attack, Federal Bureau of Investigation Director Christopher Wray announced on Wednesday, Jan. 31. The investigators also cut the routers off from other devices used in the botnet.