Security News

This Remote Access Checklist, created by Scott Matteson for TechRepublic Premium, should be used to ensure all employees have the requisite items, accounts, access, and instructions needed for...

Chinese hackers targeting large IT service providers in Southern Europe were seen abusing Visual Studio Code (VSCode) tunnels to maintain persistent access to compromised systems. [...]

A suspected China-nexus cyber espionage group has been attributed to an attacks targeting large business-to-business IT service providers in Southern Europe as part of a campaign codenamed...

With AnyViewer, savvy business owners can securely connect to remote devices without worrying about security.

Two critical security flaws impacting the Spam protection, Anti-Spam, and FireWall plugin WordPress could allow an unauthenticated attacker to install and enable malicious plugins on susceptible...
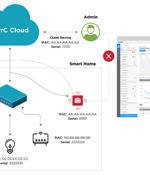
A security analysis of the OvrC cloud platform has uncovered 10 vulnerabilities that could be chained to allow potential attackers to execute code remotely on connected devices. "Attackers...

The prolific Midnight Blizzard crew cast a much wider net in search of scrummy intel Microsoft says a mass phishing campaign by Russia's foreign intelligence services (SVR) is now in its second...

Amazon has seized domains used by the Russian APT29 hacking group in targeted attacks against government and military organizations to steal Windows credentials and data using malicious Remote...

Attacks on unprotected servers reach 'critical level' An unknown attacker is abusing exposed Docker Remote API servers to deploy perfctl cryptomining malware on victims' systems, according to...
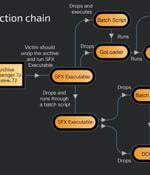
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to deliver DarkCrystal RAT (aka DCRat) and a previously...