Security News
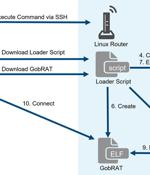
Linux routers in Japan are the target of a new Golang remote access trojan called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center said in a report published today. The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process to evade detection.

Cisco has released updates to address a set of nine security flaws in its Small Business Series Switches that could be exploited by an unauthenticated, remote attacker to run arbitrary code or cause a denial-of-service condition. Four of the nine vulnerabilities are rated 9.8 out of 10 on the CVSS scoring system, making them critical in nature.

The FBI and friends have warned organizations to "Strictly limit the use of RDP and other remote desktop services" to avoid BianLian infections and the ransomware gang's extortion attempts that follow the data encryption. BianLian typically gains access to victims' Windows systems via Remote Desktop Protocol credentials - hence the advice to shore up RDP security - and then uses software tools and command-line scripting to find and steal more credentials and snoop through the network and its files.

Cybercriminals are starting to target Microsoft's VSCode Marketplace, uploading three malicious Visual Studio extensions that Windows developers downloaded 46,600 times. According to Check Point, whose analysts discovered the malicious extensions and reported them to Microsoft, the malware enabled the threat actors to steal credentials, system information, and establish a remote shell on the victim's machine.

In an effort to solve the access-related challenges facing OT and critical infrastructure operators, the team at Cyolo built a zero-trust access platform designed to meet the unique safety, security, and uptime requirements of OT and industrial control systems environments. Let's look under the hood: #. The Cyolo solution is a high-powered combination of Zero Trust Network Access, Identity Provider, and Privileged Access Management.

Presenting at Black Hat Asia 2023, an infosec researcher detailed how remote updates can be exploited to modify voltage on a Supermicro motherboard and remotely brick machines. Voltpillager was not a remote attack and required physical proximity, such as a rogue employee, so was limited in threat scope.
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution. "Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a report.

The U.S. Cybersecurity and Infrastructure Security Agency on Tuesday released an Industrial Control Systems advisory about a critical flaw affecting ME RTU remote terminal units. The security vulnerability, tracked as CVE-2023-2131, has received the highest severity rating of 10.0 on the CVSS scoring system for its low attack complexity.

Networking equipment maker Zyxel has released patches for a critical security flaw in its firewall devices that could be exploited to achieve remote code execution on affected systems. "Improper error message handling in some firewall versions could allow an unauthenticated attacker to execute some OS commands remotely by sending crafted packets to an affected device," Zyxel said in an advisory on April 25, 2023.

A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox protections. Both the flaws - CVE-2023-29199 and CVE-2023-30547 - are rated 9.8 out of 10 on the CVSS scoring system and have been addressed in versions 3.9.16 and 3.9.17, respectively.