Security News

Fortinet urges customers to patch their appliances against an actively exploited FortiOS SSL-VPN vulnerability that could allow unauthenticated remote code execution on devices."A heap-based buffer overflow vulnerability [CWE-122] in FortiOS SSL-VPN may allow a remote unauthenticated attacker to execute arbitrary code or commands via specifically crafted requests," warns Fortinet in a security advisory released today.
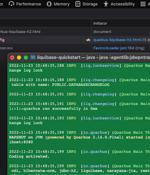
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.
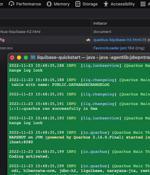
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.

Three Android applications that allow users to use devices as remote keyboards for their computers have critical vulnerabilities that could expose key presses and enable remote code execution. CVE-2022-45479 - PC Keyboard flow allowing a remote unauthenticated user to send instructions to the server to execute arbitrary code without requiring authorization or authentication.

A pre-authentication RCE flaw in Oracle Access Manager that has been fixed in January 2022 is being exploited by attackers in the wild, the Cybersecurity and Infrastructure Security Agency has confirmed by adding the vulnerability to its Known Exploited Vulnerabilities Catalog.The vulnerability is in the OpenSSO Agent component of the Oracle Access Manager product, which is widely used by corporations for single sign-on as part of the Oracle Fusion Middleware suite.

Spotify's Backstage has been discovered as vulnerable to a severe security flaw that could be exploited to gain remote code execution by leveraging a recently disclosed bug in a third-party module. The vulnerability, at its core, takes advantage of a critical sandbox escape in vm2, a popular JavaScript sandbox library, that came to light last month.

Older versions of the Spotify Backstage development portal builder are vulnerable to a critical unauthenticated remote code execution flaw allowing attackers to run commands on publicly exposed systems. Oxeye confirmed the impact in Backstage and alerted Spotify on August 18, 2022.
Microsoft on Tuesday said it addressed an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB that enabled full read and write access. The tech giant said the problem was introduced on August 12, 2022, and rectified worldwide on October 6, 2022, two days after responsible disclosure from Orca Security, which dubbed the flaw CosMiss. "In short, if an attacker had knowledge of a Notebook's 'forwardingId,' which is the UUID of the Notebook Workspace, they would have had full permissions on the Notebook without having to authenticate, including read and write access, and the ability to modify the file system of the container running the notebook," researchers Lidor Ben Shitrit and Roee Sagi said.

Analysts at Orca Security have found a critical vulnerability affecting Azure Cosmos DB that allowed unauthenticated read and write access to containers.Named CosMiss, the security issue is in Azure Cosmos DB built-in Jupyter Notebooks that integrate into the Azure portal and Azure Cosmos DB accounts for querying, analyzing, and visualizing NoSQL data and results easier.

IT service management software platform ConnectWise has released Software patches for a critical security vulnerability in Recover and R1Soft Server Backup Manager. ConnectWise's advisory notes that the flaw affects Recover v2.9.7 and earlier, as well as R1Soft SBM v6.16.3 and earlier, are impacted by the critical flaw.