Security News

The FBI dismantled the Warzone RAT malware operation, seizing infrastructure and arresting two individuals associated with the cybercrime operation. Warzone RAT is commodity malware created in 2018 that offers numerous features to aid cybercrime, including UAC bypass, hidden remote desktop, cookie and password stealing, keylogging, webcam recording, file operations, reverse proxy, remote shell, and process management.
The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used to sell a remote access trojan (RAT) called Warzone RAT. The domains – www.warzone[.]ws and...

Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a modified version of an open-source remote access trojan called AllaKore RAT. The BlackBerry...
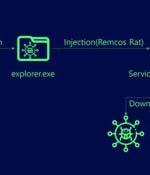
The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards by disguising it as adult-themed games in South Korea. WebHard, short for web hard drive, is a...

Threat actors operating under the name Anonymous Arabic have released a remote access trojan (RAT) called Silver RAT that’s equipped to bypass security software and stealthily launch hidden...

A new variant of remote access trojan called Bandook has been observed being propagated via phishing attacks with an aim to infiltrate Windows machines, underscoring the continuous evolution of...
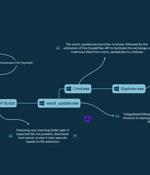
The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT using new strategies to evade detection from security software. "The group's weapon of choice is Remcos...

North Korea-backed group Lazarus has been spotted exploiting the Log4Shell vulnerability and novel malware written in DLang. "This campaign consists of continued opportunistic targeting of enterprises globally that publicly host and expose their vulnerable infrastructure to n-day vulnerability exploitation such as CVE-2021-44228. We have observed Lazarus target manufacturing, agricultural and physical security companies," Cisco Talos researchers shared.

The notorious North Korean hacking group known as Lazarus continues to exploit CVE-2021-44228, aka "Log4Shell," this time to deploy three previously unseen malware families written in DLang. The new malware are two remote access trojans named NineRAT and DLRAT and a malware downloader named BottomLoader.

Security researchers discovered a remote access trojan they named Krasue that is targeting Linux systems of telecommunications companies and managed to remain undetected since 2021. According to researchers at cybersecurity company Group-IB, the main function of the malware is to maintain access to the host, which may suggest that it is deployed through a botnet or sold by initial access brokers to threat actors seeking access to a particular target.