Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

A new malware distribution campaign uses fake Google Chrome, Word, and OneDrive errors to trick users into running malicious PowerShell "Fixes" that install malware. Now the overlays display fake Google Chrome, Microsoft Word, and OneDrive errors.

Microsoft on Wednesday outlined its plans to deprecate Visual Basic Script (VBScript) in the second half of 2024 in favor of more advanced alternatives such as JavaScript and PowerShell....

A threat actor is using a PowerShell script that was likely created with the help of an artificial intelligence system such as OpenAI's ChatGPT, Google's Gemini, or Microsoft's CoPilot. Accessing the shortcut file triggered PowerShell to run a remote script.
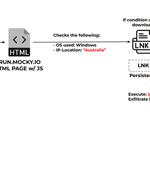
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium. "In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang's Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs," security researchers Niraj Shivtarkar and Avinash Kumar said.

Lax policies for package naming on Microsoft's PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular packages and potentially lay the ground for massive supply chain attacks. PowerShell Gallery is a Microsoft-run online repository of packages uploaded by the wider PowerShell community, hosting a large number of scripts and cmdlet modules for various purposes.
Active flaws in the PowerShell Gallery could be weaponized by threat actors to pull off supply chain attacks against the registry's users. "These flaws make typosquatting attacks inevitable in this registry, while also making it extremely difficult for users to identify the true owner of a package," Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman said in a report shared with The Hacker News.

Symantec's threat research team, part of Broadcom, reports today that the threat actors have recently begun using USB malware to propagate to additional systems inside infected networks. Symantec's analysts report that Gamaredon's 2023 activity spiked between February and March 2023, while the hackers continued to maintain a presence on some compromised machines until May 2023.

A new PowerShell malware script named 'PowerDrop' has been discovered to be used in attacks targeting the U.S. aerospace defense industry. PowerDrop was discovered by Adlumin, who last month found a sample of the malware in the network of a defense contractor in the U.S. The firm reports that PowerDrop uses PowerShell and WMI to create a persistent RAT on the breached networks.

Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors using built-in data exfiltration methods like negate the need to bring in external tools that might be flagged by security software and/or human-based security detection mechanisms," Palo Alto Networks Unit 42 researcher Ryan Chapman said.