Security News > 2023 > September > Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows
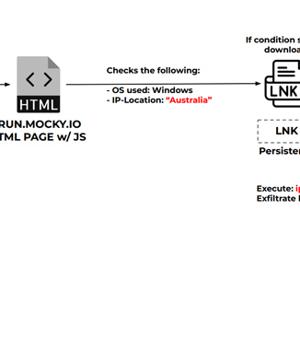
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium.
"In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang's Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs," security researchers Niraj Shivtarkar and Avinash Kumar said.
Nishang is a framework and collection of PowerShell scripts and payloads for offensive security, penetration testing, and red teaming.
NTLMv2 hash stealing infection chain, which employs a custom version of the aforementioned Start-CaptureServer PowerShell script to harvest NTLMv2 hashes.
Windows update infection chain, which targets Belgium users with fake Windows update scripts designed to run commands like tasklist and systeminfo.
"The threat actors' custom PowerShell scripts and strategic use of LNK files within ZIP archives highlights their technical expertise," the researchers said.
News URL
https://thehackernews.com/2023/09/cybercriminals-using-powershell-to.html