Security News

A new Ducktail phishing campaign is spreading a never-before-seen Windows information-stealing malware written in PHP used to steal Facebook accounts, browser data, and cryptocurrency wallets. The malware targeted information stored in browsers, focusing on Facebook Business account data, and exfiltrated it to a private Telegram channel that acted as a C2 server.
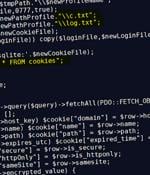
A PHP version of an information-stealing malware called Ducktail has been discovered in the wild being distributed in the form of cracked installers for legitimate apps and games, according to the latest findings from Zscaler. "Like older versions, the latest version also aims to exfiltrate sensitive information related to saved browser credentials, Facebook account information, etc.," Zscaler ThreatLabz researchers Tarun Dewan and Stuti Chaturvedi said.

Researchers have disclosed details about a now-patched high-severity security flaw in Packagist, a PHP software package repository, that could have been exploited to mount software supply chain attacks. Packagist is used by the PHP package manager Composer to determine and download software dependencies that are included by developers in their projects.

Threat analysts have uncovered a large-scale campaign targeting Elastix VoIP telephony servers with more than 500,000 malware samples over a period of three months. Security researchers at Palo Alto Networks' Unit 42 say that the attackers' goal was to plant a PHP web shell that could run arbitrary commands on the compromised communications server.

QNAP, Taiwanese maker of network-attached storage devices, on Wednesday said it's in the process of fixing a critical three-year-old PHP vulnerability that could be abused to achieve remote code execution. "A vulnerability has been reported to affect PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24, and 7.3.x below 7.3.11 with improper nginx config," the hardware vendor said in an advisory.

QNAP has warned customers today that most of its Network Attached Storage devices are vulnerable to attacks that would exploit a three-year-old critical PHP vulnerability allowing remote code execution. "A vulnerability has been reported to affect PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24, and 7.3.x below 7.3.11. If exploited, the vulnerability allows attackers to gain remote code execution," QNAP explained in a security advisory released today.

Two trojanized Python and PHP packages have been uncovered in what's yet another instance of a software supply chain attack targeting the open source ecosystem. One of the packages in question is "Ctx," a Python module available in the PyPi repository.
A keen-eyed researcher at SANS recently wrote about a new and rather specific sort of supply chain attack against open-source software modules in Python and PHP. Following on-line discussions about a suspicious public Python module, Yee Ching Tok noted that a package called ctx in the popular PyPi repository had suddenly received an "Update", despite not otherwise being touched since late 2014. In theory, of course, there's nothing wrong with old packages suddenly coming back to life.

Yesterday, developers took notice of two hugely popular Python and PHP libraries, respectively, 'ctx' and 'PHPass' that had been hijacked, as first reported in the news by BleepingComputer. According to the hacker, rather "Security researcher," this was a bug bounty exercise and no malicious activity was intended.

The threat actor even replaced the older, safe versions of 'ctx' with code that exfiltrates the developer's environment variables, to collect secrets like Amazon AWS keys and credentials. Versions of a 'phpass' fork published to the PHP/Composer package repository Packagist had been altered to steal secrets in a similar fashion.