Security News
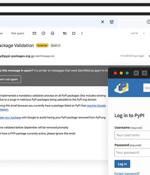
The Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims to steal developer credentials and inject malicious updates to legitimate packages. "This is the first known phishing attack against PyPI," the maintainers of the official third-party software repository said in a series of tweets.

Threat actors are increasingly abusing legitimate software-as-a-service platforms like website builders and personal branding spaces to create malicious phishing websites that steal login credentials. Because SaaS platforms simplify and streamline the process of creating new sites, phishing actors can easily switch to different themes, scale up or diversify their operations, and quickly respond to reports and takedowns.

Abnormal Security released a report which explores the current email threat landscape. This Help Net Security video provides insight into the latest advanced email attack trends.

From there they can send phishing messages carrying the AWS name into corporate emails systems to both get past scanners that typically would block suspicious messages and to add greater legitimacy to fool victims, according to email security vendor Avanan. In a report this week, researchers with Avanan - acquired last year by cybersecurity company Check Point - outlined a phishing campaign that uses AWS and unusual syntax construction in the messages to get past scanners.

How phishing attacks are exploiting Amazon Web Services. Cybercriminals prefer to use legitimate sites and services in their phishing scams, not just to trick unsuspecting victims but to sneak past security scanners that would otherwise block traffic from a suspicious site.

Microsoft on Monday revealed it took steps to disrupt phishing operations undertaken by a "Highly persistent threat actor" whose objectives align closely with Russian state interests. "SEABORGIUM intrusions have also been linked to hack-and-leak campaigns, where stolen and leaked data is used to shape narratives in targeted countries," Microsoft's threat hunting teams said.

Hackers are increasingly moving towards hybrid forms of phishing attacks that combine email and voice social engineering calls as a way to breach corporate networks for ransomware and data extortion attacks. According to Agari's Q2 2022 cyber-intelligence report, phishing volumes have only increased by 6% compared to Q1 2022.

Abnormal Security released a which report explores the current email threat landscape and provides insight into the latest advanced email attack trends, including increases in business email compromise, the evolution of financial supply chain compromise and the rise of brand impersonation in credential phishing attacks. The research found a 48% increase in email attacks over the previous six months, and 68.5% of those attacks included a credential phishing link.

Customer engagement platform Twilio on Monday disclosed that a "Sophisticated" threat actor gained "Unauthorized access" using an SMS-based phishing campaign aimed at its staff to gain information on a "Limited number" of accounts. The social-engineering attack was bent on stealing employee credentials, the company said, calling the as-yet-unidentified adversary "Well-organized" and "Methodical in their actions." The incident came to light on August 4.

Three different offshoots of the notorious Conti cybercrime cartel have resorted to the technique of call-back phishing as an initial access vector to breach targeted networks. "Three autonomous threat groups have since adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology," cybersecurity firm AdvIntel said in a Wednesday report.