Security News
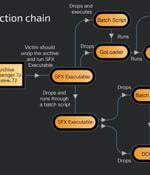
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to deliver DarkCrystal RAT (aka DCRat) and a previously...
Two malware families that suffered setbacks in the aftermath of a coordinated law enforcement operation called Endgame have resurfaced as part of new phishing campaigns. Bumblebee and Latrodectus,...

Phishing scams aimed at voters, malicious domain registrations impersonating candidates, and other threat activity designed to exploit unassuming victims take center stage as the US election...

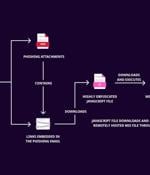
A new spear-phishing campaign targeting Brazil has been found delivering a banking malware called Astaroth (aka Guildma) by making use of obfuscated JavaScript to slip past security guardrails....

A new tax-themed malware campaign targeting insurance and finance sectors has been observed leveraging GitHub links in phishing email messages as a way to bypass security measures and deliver...

Winter is coming The US Department of Justice and Microsoft have seized 107 websites used by Russian cyberspies in a phishing campaign to steal sensitive information from US government agencies,...

INTERPOL has announced the arrest of eight individuals in Côte d'Ivoire and Nigeria as part of a crackdown on phishing scams and romance cyber fraud. Dubbed Operation Contender 2.0, the initiative...
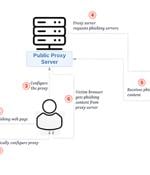
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past year, indicating that it's being used by a large number of...

Mimecast tells TechRepublic that AI may exacerbate phishing risks in Australia.

Phishing attacks are becoming more advanced and harder to detect, but there are still telltale signs that can help you spot them before it's too late. See these key indicators that security...