Security News

TechRepublic Premium Penetration Testing and Scanning Policy System or network vulnerabilities and security threats can severely impact business operations or even shutter its doors. The purpose of this policy from TechRepublic Premium is to provide guidelines for appropriate penetration testing and scanning of computer systems and networks.

TechRepublic Premium Penetration Testing and Scanning Policy System or network vulnerabilities and security threats can severely impact business operations or even shutter its doors. The purpose of this policy from TechRepublic Premium is to provide guidelines for appropriate penetration testing and scanning of computer systems and networks.
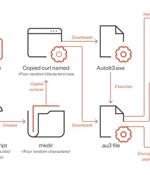
A piece of malware known as DarkGate has been observed being spread via instant messaging platforms such as Skype and Microsoft Teams. In these attacks, the messaging apps are used to deliver a...
Cybersecurity researchers have called attention to a new antivirus evasion technique that involves embedding a malicious Microsoft Word file into a PDF file. The sneaky method, dubbed MalDoc in PDF by JPCERT/CC, is said to have been employed in an in-the-wild attack in July 2023.

Japan's computer emergency response team is sharing a new 'MalDoc in PDF' attack detected in July 2023 that bypasses detection by embedding malicious Word files into PDFs. The file sampled by JPCERT is a polyglot recognized by most scanning engines and tools as a PDF, yet office applications can open it as a regular Word document. The malicious documents in this campaign are a combination of PDF and Word documents, which can be opened as either file format.

Ghostscript, an open-source interpreter for PostScript language and PDF files widely used in Linux, has been found vulnerable to a critical-severity remote code execution flaw. The flaw is tracked as CVE-2023-3664, having a CVSS v3 rating of 9.8, and impacts all versions of Ghostscript before 10.01.2, which is the latest available version released three weeks ago.

A researcher has published a working exploit for a remote code execution flaw impacting ReportLab Toolkit, a popular Python library used by numerous projects to generate PDF files from HTML input. ReportLab Toolkit is used by multiple projects as a PDF library and has approximately 3.5 million monthly downloads on PyPI. The problem stems from the ability to bypass sandbox restrictions on 'rl safe eval,' whose role is to prevent malicious code execution, leading to the attacker accessing potentially dangerous Python built-in functions.

QBot malware is now distributed in phishing campaigns utilizing PDFs and Windows Script Files to infect Windows devices. Qbot is a former banking trojan that evolved into malware that provides initial access to corporate networks for other threat actors.

Microsoft and Adobe have partnered to integrate the Adobe Acrobat PDF rendering engine directly into the Edge browser, replacing the existing PDF engine. Starting in March 2023, new versions of Microsoft Edge for Windows 10 and Windows 11 will roll out that includes this new PDF engine.

Current cybersecurity practices are woefully unprepared to meet the complexities of modern networks. Cloud services, remote users, personally-owned devices, mobile company assets and other forms of tech regularly move from outside the network in, and a once-safe device can't be assumed to be safe again.