Security News

Fortinet has revealed that threat actors have found a way to maintain read-only access to vulnerable FortiGate devices even after the initial access vector used to breach the devices was patched....

Microsoft is rolling out a new generation of AI agents in Security Copilot, built to help with some of the most time-consuming security challenges, such as phishing, data protection, and identity...

Despite two patching attempts, a security issue that may allow attackers to compromise Windows user’s NTLM (authentication) credentials via a malicious Windows themes file still affects...

CISA wants you to leap on Citrix and Ivanti issues. Adobe, Intel, SAP also bid for patching priorities Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant news that there...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
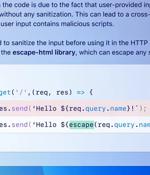
GitHub on Wednesday announced that it's making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort...

CVE Prioritizer is an open-source tool designed to assist in prioritizing the patching of vulnerabilities. The tool leverages the correlation between CVSS and EPSS scores to improve efforts in fixing vulnerabilities.

JetBrains is encouraging all users of TeamCity to upgrade to the latest version following the disclosure of a critical vulnerability in the CI/CD tool. The vulnerability only requires attention for admins of on-prem servers since TeamCity Cloud has already been patched.

Blind spots and critical vulnerabilities are worsening, with 45% of critical CVEs remaining unpatched.The educational services industry has a significantly higher percentage of servers with unpatched weaponised Common Vulnerabilities and Exposures, compared to the general average of 10%. Industries still using end-of-life or EoS OSs that are no longer actively supported or patched for vulnerabilities and security issues by the manufacturer: Educational services, retail trade, healthcare, manufacturing and public administration.