Security News

As ransomware crews increasingly shift beyond just encrypting victims' files and demanding a payment to unlock them, instead swiping sensitive info straight away, some of the more mature crime organizations are developing custom malware for their data theft. "Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," the report's authors note.

Google announced today that passkeys are now available for high-risk users when enrolling in the Advanced Protection Program, which provides the strongest level of account security. The Advanced Protection Program is a free service that protects the accounts of users such as activists, journalists, business leaders, and political teams, who are at a higher risk of being targeted by online attacks.

After publication of my "Kryptonite" article about a prompt that crashes many AI chatbots, I began to get a steady stream of emails from readers - many times the total of all reader emails I'd received in the previous decade. Disappointingly, too many of them consisted of little more than a request to reveal the prompt so that they could lay waste to large language models.

Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that's widely used by cybercriminals in Southeast Asia, particularly those linked to pig butchering scams. The British blockchain analytics firm said that the marketplace is part of HuiOne Group, a Cambodian conglomerate with links to Cambodia's ruling Hun family and that another HuiOne business, HuiOne International Payments, is actively involved in laundering scam proceeds globally.

Theregister.com needs to review the security of your connection before proceeding. Theregister.com to respond.....
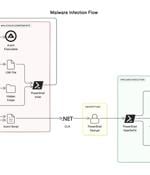
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations," Trellix security researchers Mathanraj Thangaraju and Sijo Jacob said.

As cyber threats evolve and increase in volume, traditional approaches for stymieing cyber threats are no longer sufficient. CISOs must prioritize diversity in their teams to counter evolving threats.

In this Help Net Security interview, Jake King, Head of Threat & Security Intelligence at Elastic, discusses companies' exposure to new security risks and vulnerabilities as they rush to deploy LLMs. King explains how LLMs pose significant risks to data privacy and outlines strategies for mitigating these security risks. While many companies are jumping on the generative AI bandwagon and rushing to deploy LLMs as quickly as they can, this has increased their exposure to new risks and vulnerabilities.

BunkerWeb is an open-source Web Application Firewall distributed under the AGPLv3 free license. The solution's core code is entirely auditable by a third party and the community.

As a Cyber Security Engineer, you will perform research in the areas of cyber and network security, advise DoD and IC space system customers on secure design and implementation of systems, review network architecture designs identify security, dataflow, performance deficiencies. As a Datacenter Security Operations Manager, you will oversee the implementation of physical security policies and procedures at applicable datacenters, ensuring Microsoft's physical security vendor guard force has the resources and information to deliver physical security services that meet Microsoft and customer requirements to protect people, information, and critical infrastructure.