Security News

Despite a plethora of available security solutions, more and more organizations fall victim to Ransomware and other threats. These continued threats aren't just an inconvenience that hurt...
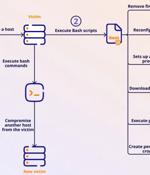
Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been observed on the Google Play Store. The...

The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection evasion techniques, enabling its operators to remotely interact with...

They are based on cyber-attack scenarios and are used by facilitators to guide participants throughout the cybersecurity exercise. Before designing a cyber exercise scenario, the controller should assess any potential constraints on resources, skills or budget for running certain types of exercises.

The average malware detections rose 80% from the previous quarter, illustrating a substantial volume of malware threats arriving at the network perimeter. Geographically, most of the increased malware instances affected the Americas and Asia-Pacific.

One of the primary concerns regarding data privacy is the potential for breaches and unauthorized access. Whether it's financial records, medical histories, or personal communications, individuals have a right to control who can access their data and for what purposes.

The latest addition to GitGuardian's code security platform equips security and developer teams with a unified vulnerability remediation solution, capitalizing on cross-team collaboration, incident visibility, and context. Security teams can use Sentra Jagger to get insights and recommendations on specific security actions through an interactive, user-friendly interface.

Of course it was before 2008, when we created the Security and Human Behavior workshop. It was well before 2001, when we created the Workshop on Economics and Information Security.

The problem, he found, was in the liblzma data compression library, which is part of the XZ package, and he concluded that "The upstream xz repository and the xz tarballs have been backdoored."Which Linux distributions have been affected by the backdoored XZ packages?

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.