Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Since April, millions of phishing emails have been sent through the Phorpiex botnet to conduct a large-scale LockBit Black ransomware campaign. The LockBit Black encryptor deployed in these attacks is likely built using the LockBit 3.0 builder leaked by a disgruntled developer on Twitter in September 2022.

Most IT and security teams would agree that ensuring endpoint security and network access security applications are running in compliance with security policies on managed PCs should be a basic task. The 2024 Cyber Resilience Risk Index report found that, if not supported by automated remediation technologies, top endpoint protection platforms and network access security applications are failing to maintain compliance with security policies 24% of the time across its sample of managed PCs. When combined with data showing significant delays in patching applications, Absolute Security argued organisations may be ill-equipped to make the landmark shift to AI PCs, which would require significant resourcing and direct attention away from these foundations of cyber security.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
DNS tunneling is the encoding of data or commands that are sent and retrieved via DNS queries, essentially turning DNS, a fundamental network communication component, into a covert communications channel. Hackers commonly use DNS tunneling to bypass network firewalls and filters, employing the technique for command and control and Virtual Private Network operations.

The negative press, coupled with YouTube horror stories, has cemented the Dark Web's reputation for illicit behavior. Today, the Dark Web is believed to be a platform where cybercriminals sell drugs, weapons, malicious software and piles of consumer and sensitive corporate data.

Ray Fernandez, writing for TechRepublic Premium, presents this DevSecOps glossary to help you navigate the modern world of software development and enhance your understanding. Unlike traditional rate limiting, which only limits users based on the client's IP address, advanced rate limiting can take into account other factors, such as the client's account ID, API key or even the content of the request.

The City of Helsinki is investigating a data breach in its education division, which it discovered in late April 2024, impacting tens of thousands of students, guardians, and personnel."Considering the number of users in the city's services now and in previous years, in the worst case, this data breach affects over 80,000 students and their guardians."

Top encryption software: Comparison table Top encryption software BitLocker: Best for Windows environments. Trend Micro Endpoint Encryption offers high quality enterprise-wide full disk encryption, as well as file and database encryption.
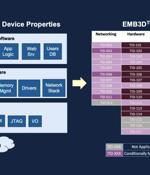
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. "The model provides a...