Security News

FuzzyAI is an open-source framework that helps organizations identify and address AI model vulnerabilities in cloud-hosted and in-house AI models, like guardrail bypassing and harmful output...

Keycloak is an open-source project for identity and access management (IAM). It provides user federation, strong authentication, user management, authorization, and more. Keycloak is based on...

Sonatype’s 2024 Open Source Malware Threat Report reveals that the number of malicious packages has surpassed 778,500 since tracking began in 2019. In 2024, researchers examined how threat actors...

Neosync is an open-source, developer-centric solution designed to anonymize PII, generate synthetic data, and synchronize environments for improved testing and debugging. What you can do with...
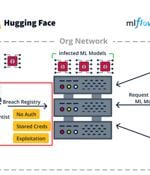
Cybersecurity researchers have disclosed multiple security flaws impacting open-source machine learning (ML) tools and frameworks such as MLflow, H2O, PyTorch, and MLeap that could pave the way...

SafeLine is an open-source and self-hosted Web Application Firewall (WAF) that protects websites from cyber attacks. “SafeLine WAF was created to protect web applications for small and...

The geographic distribution of open-source contributions introduces geopolitical risks that organizations must urgently consider, especially with rising nation-state attacks, according to Lineaje....
Nextcloud has unveiled Nextcloud Talk, an open-source alternative to Microsoft Teams. It’s a privacy-compliant collaboration platform for hybrid teams that gives companies complete control over...

This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. ScubaGear ScubaGear is an open-source...

Google has revealed that its AI-powered fuzzing tool, OSS-Fuzz, has been used to help identify 26 vulnerabilities in various open-source code repositories, including a medium-severity flaw in the...