Security News
CoinStats suffered a massive security breach that compromised 1,590 cryptocurrency wallets, with the attack suspected to have been carried out by North Korean threat actors. For users who want to use the portfolio management features, the platform requires read-only access to connected external crypto wallets and were not affected by the breach.

Threat actors linked to North Korea have accounted for one-third of all the phishing activity targeting Brazil since 2020, as the country's emergence as an influential power has drawn the...

Microsoft has named yet another state-aligned threat actor: Moonstone Sleet, which engages in cyberespionage and ransomware attacks to further goals of the North Korean regime. "Moonstone Sleet uses tactics, techniques, and procedures also used by other North Korean threat actors over the last several years, highlighting the overlap among these groups," Microsoft's threat analysts say.

A never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting individuals and organizations in the software and information...

Microsoft has linked a North Korean hacking group it tracks as Moonstone Sleet to FakePenny ransomware attacks, which have led to millions of dollars in ransom demands. Unlike previous ransomware attacks coordinated by North Korean state hackers, in which victims were asked to pay $100,000, the ransom demanded by the Moonstone Sleet attackers was $6.6 million in BTC. Microsoft's assessment of this attack concluded that Moonstone Sleet's primary motivation for deploying the ransomware was financial gain.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The US Justice Department had unsealed charges against a US woman and an Ukranian man who, along with three unidentified foreign nationals, have allegedly helped North Korean IT workers work remotely for US companies under assumed US identities and thus evade sanctions. According to the court documents, the conspirators defrauded over 300 US companies by using US payment platforms and online job site accounts, proxy computers located in the United States, and witting and unwitting US persons and entities.

They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government "To infiltrate U.S. job markets through fraud in an effort to raise revenue for the North Korean government and its illicit nuclear program." Today, the U.S. State Department announced a reward of up to $5 million for any information related to Chapman's co-conspirators, the North Korean IT workers charged today, and their manager, only known as Zhonghua.
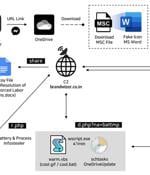
The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers...
The North Korean threat actor tracked as Kimsuky has been observed deploying a previously undocumented Golang-based malware dubbed Durian as part of highly-targeted cyber attacks aimed at South...