Security News

The U.S. Department of the Treasury has sanctioned the Sinbad cryptocurrency mixing service for its use as a money-laundering tool by the North Korean Lazarus hacking group. Today, the Treasury's Office of Foreign Assets Control has sanctioned Sinbad.io for its alleged use by North Korean hackers who have performed large-scale crypto heists, leading to hundreds of millions of dollars in losses.
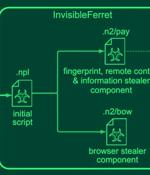
North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations...

State-sponsored threat actors from the Democratic People's Republic of Korea (DPRK) have been found targeting blockchain engineers of an unnamed crypto exchange platform via Discord with a novel...

State-sponsored North Korean hackers have significantly intensified their focus on the IT sector in recent years, by infiltrating firms developing software and companies lookind for IT workers. "In past operations, Diamond Sleet and other North Korean threat actors have successfully carried out software supply chain attacks by infiltrating build environments," Microsoft noted.

The U.S. government has announced the seizure of 17 website domains used by North Korean information technology (IT) workers as part of an illicit scheme to defraud businesses across the world,...
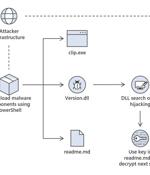
North Korean threat actors are actively exploiting a critical security flaw in JetBrains TeamCity to opportunistically breach vulnerable servers, according to Microsoft. The attacks, which entail...

Microsoft says that the North Korean Lazarus and Andariel hacking groups are exploiting the CVE-2023-42793 flaw in TeamCity servers to deploy backdoor malware, likely to conduct software supply chain attacks. In September, TeamCity fixed a critical 9.8/10 vulnerability tracked as CVE-2023-42793 that allowed unauthenticated attackers to remotely execute code.

ALSO: Verizon turns self in for reduced fine, malvertising comes to macOS, and this week's critical vulnerabilities In brief Watch out, cyber security researchers: Suspected North Korean-backed...

North Korean threat actors are once again attempting to compromise security researchers' machines by employing a zero-day exploit. The warning comes from Google's own security researchers Clement Lecigne and Maddie Stone, who detailed the latest campaign mounted by government-backed attackers.

Threat actors associated with North Korea are continuing to target the cybersecurity community using a zero-day bug in unspecified software over the past several weeks to infiltrate their machines. A search on X shows that the now-suspended account has been active since at least October 2022, with the actor releasing proof-of-concept exploit code for high-severity privilege escalation flaws in the Windows Kernel such as CVE-2021-34514 and CVE-2022-21881.