Security News

A previously undocumented threat actor known as Silent Lynx has been linked to cyber attacks targeting various entities in Kyrgyzstan and Turkmenistan. "This threat group has previously targeted...

Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.
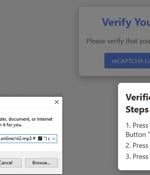
Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA verification checks to deliver the infamous Lumma information stealer. "The campaign is...

The U.S. Department of Justice (DoJ) on Tuesday disclosed that a court-authorized operation allowed the Federal Bureau of Investigation (FBI) to delete PlugX malware from over 4,250 infected...

Japan's National Police Agency (NPA) and National Center of Incident Readiness and Strategy for Cybersecurity (NCSC) accused a China-linked threat actor named MirrorFace of orchestrating a...

A little-known cyber espionage actor known as The Mask has been linked to a new set of attacks targeting an unnamed organization in Latin America twice in 2019 and 2022. "The Mask APT is a...

GitGuardian takes on enterprise secrets sprawl Partner Content With Non-Human Identities (NHIs) now outnumbering human users 100 to one in enterprise environments, managing secrets across multiple...

Are you using the cloud or thinking about transitioning? Undoubtedly, multi-cloud and hybrid environments offer numerous benefits for organizations. However, the cloud's flexibility, scalability,...

Multi-stage cyber attacks, characterized by their complex execution chains, are designed to avoid detection and trick victims into a false sense of security. Knowing how they operate is the first...

Five alleged members of the infamous Scattered Spider cybercrime crew have been indicted in the U.S. for targeting employees of companies across the country using social engineering techniques to...