Security News
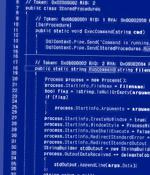
Poorly managed Microsoft SQL servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware. "Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behavior," AhnLab Security Emergency response Center said in a report published last week.

A large-scale attack campaign discovered in the wild has been exploiting Kubernetes Role-Based Access Control to create backdoors and run cryptocurrency miners. The Israeli company, which dubbed the attack RBAC Buster, said it found 60 exposed K8s clusters that have been exploited by the threat actor behind this campaign.

Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023. "The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet," CrowdStrike said in a new report shared with The Hacker News.

Pics A Massachusetts man accused of using his job as a city's assistant facilities director to hide a cryptocurrency mining operation in the crawlspace of a school has surrendered himself to authorities on Friday morning after skipping his Thursday arraignment. A judge issued a default warrant for Nadeam Nahas' arrest yesterday on charges of fraudulent use of electricity and vandalizing a school, in relation with the cryptomining operation discovered under Cohasset Middle/High School in December, 2021.
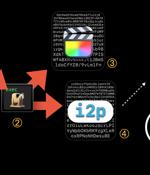
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. "This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.

An active malware campaign has set its sights on Facebook and YouTube users by leveraging a new information stealer to hijack the accounts and abuse the systems' resources to mine cryptocurrency. Bitdefender is calling the malware S1deload Stealer for its use of DLL side-loading techniques to get past security defenses and execute its malicious components.

A new malware dubbed 'ProxyShellMiner' exploits the Microsoft Exchange ProxyShell vulnerabilities to deploy cryptocurrency miners throughout a Windows domain to generate profit for the attackers. ProxyShell is the name of three Exchange vulnerabilities discovered and fixed by Microsoft in 2021.

A cryptocurrency mining attack targeting the Linux operating system also involved the use of an open source remote access trojan (RAT) dubbed CHAOS. The threat, which was spotted by Trend Micro in...

An ongoing analysis into an up-and-coming cryptocurrency mining botnet known as KmsdBot has led to it being accidentally taken down. The botnet strikes both Windows and Linux devices spanning a wide range of microarchitectures with the primary goal of deploying mining software and corralling the compromised hosts into a DDoS bot.

An ongoing analysis into an up-and-coming cryptocurrency mining botnet known as KmsdBot has led to it being accidentally taken down. The botnet strikes both Windows and Linux devices spanning a wide range of microarchitectures with the primary goal of deploying mining software and corralling the compromised hosts into a DDoS bot.