Security News

In its latest quarterly threat report, Meta said it had detected and disrupted influence operations originating in the US, and it calls out those it believes are responsible: the American military. Meta said it picked up on three major covert influence operations on its platforms in the third quarter of the year, the first of which originated in the United States.

Meta has removed several accounts on Facebook and Instagram associated with the U.S. military, saying they were used as part of covert influence operations targeting the Middle East and Russia. Meta says it removed 39 Facebook accounts, 26 Instagram accounts, 16 Facebook Pages, and two Facebook groups for violating its 'coordinated inauthentic behavior' policy.

A series of attacks targeting transportation and logistics organizations in Ukraine and Poland with Prestige ransomware since October have been linked to an elite Russian military cyberespionage group. Researchers with Microsoft Security Threat Intelligence pinned the ransomware attacks on the Russian Sandworm threat group based on forensic artifacts and victimology, tradecraft, capabilities, and infrastructure overlapping with the group's previous activity.

The threat actor behind a remote access trojan called RomCom RAT has been observed targeting Ukrainian military institutions as part of a new spear-phishing campaign that commenced on October 21, 2022. "Once the victim installs a Trojanized bundle, it drops RomCom RAT to the system."

Spies for months hid inside a US military contractor's enterprise network and stole sensitive data, according to a joint alert from the US government's Cybersecurity and Infrastructure Security Agency, the FBI, and NSA. The intruders somehow broke into the defense org's Microsoft Exchange Server - the Feds still aren't sure how - and rummaged through mailboxes for hours and used a compromised admin account to query Exchange via its EWS API. The snoops also ran Windows commands to learn more about the IT setup and gathered up files into archives using WinRAR. Interestingly, the cyberattackers also used the open source network toolkit Impacket to remote-control machines on the network and move laterally. It seems someone eventually realized something was up because from November 2021 to January 2022, CISA and a "Trusted third-party" security company were called in to check over the contractor's enterprise network in an incident response.
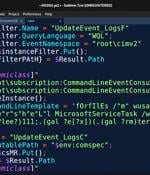
A new covert attack campaign singled out multiple military and weapons contractor companies with spear-phishing emails to trigger a multi-stage infection process designed to deploy an unknown payload on compromised machines. "The attack was carried out starting in late summer 2022 targeting at least two high-profile military contractor companies," Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in an analysis.

Security researchers have discovered a new campaign targeting multiple military contractors involved in weapon manufacturing, including an F-35 Lightning II fighter aircraft components supplier. The campaign stands out for its secure C2 infrastructure and multiple layers of obfuscation in the PowerShell stagers.

China has accused the U.S. National Security Agency of conducting a string of cyberattacks aimed at aeronautical and military research-oriented Northwestern Polytechnical University in the city of Xi'an in June 2022. The National Computer Virus Emergency Response Centre disclosed its findings last week, and accused the Office of Tailored Access Operations at the USA's National Security Agency of orchestrating thousands of attacks against the entities located within the country.

China has accused the United States of a savage cyber-attack on a university famed for conducting aerospace research and linked to China's military. The National Computer Virus Emergency Response Centre made its accusation on September 5th, claiming that the Office of Tailored Access Operation at the USA's National Security Agency has unleashed over 10,000 attacks in China, some using zero-day exploits, and lifted 140GB of "High value data".

Russia's military has praised civilian grade Chinese-made drones and robots for having performed well on the battlefield, leading their manufacturers to point out the equipment is not intended or sold for military purposes. "When assembling the M-81, Chinese technologies are used, the cost is 1 million rubles. The company plans to launch production in Russia," reported Russian tech media source iXBT. In late July, Unitree tweeted that it "Opposes any form of refit and behavior that is harmful or potentially harmful for human beings" and that it only manufactures and sells civilian products.