Security News

Microsoft has patched a misconfiguration issue impacting the Azure Active Directory identity and access management service that exposed several "High-impact" applications to unauthorized access. "One of these apps is a content management system that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users," cloud security firm Wiz said in a report.

Microsoft has added Security Copilot, a natural language chatbot that can write and analyze code, to its suite of products enabled by OpenAI's GPT-4 generative AI model. Microsoft will release more information through its email updates about when Security Copilot might become generally available.

Microsoft has shared more information on what malicious embedded files OneNote will soon block to defend users against ongoing phishing attacks pushing malware.While previously, OneNote warned users that opening attachments could harm their data but still allowed them to open the embedded files tagged as dangerous, after the security improvement rolls out, users will no longer have the choice to open files with dangerous extensions.

Microsoft says a new Windows 11 preview build rolling out today will allow Insiders to test the company's adaptive brightness feature on more systems. While Content Adaptive Brightness Control could previously only be used on laptops while running on battery, CABC can now also be toggled on plugged-in devices.
A misconfigured Microsoft application allowed anyone to log in and modify Bing.com search results in real-time, as well as inject XSS attacks to potentially breach the accounts of Office 365 users. Wiz researchers found that when creating an application in Azure App Services and Azure Functions, the app can be mistakenly configured to allow users from any Microsoft tenant, including public users, to log in to the application.
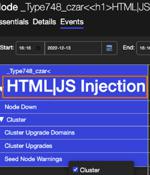
Details have emerged about a now-patched vulnerability in Azure Service Fabric Explorer that could lead to unauthenticated remote code execution. Tracked as CVE-2023-23383, the issue has been dubbed "Super FabriXss" by Orca Security, a nod to the FabriXss flaw that was fixed by Microsoft in October 2022.

Some Exchange Online users who have the RPS feature turned off by Microsoft can now have it re-enabled - at least until September when the tool is retired. Microsoft is moving all of its Exchange Online tenants from the legacy - and increasingly insecure - Remote PowerShell Protocol to the PowerShell v3 module.
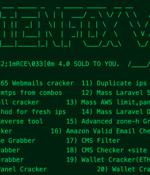
A new "Comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. "The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.

Microsoft's at-times-glitchy Defender service is again causing headaches for IT admins by flagging legitimate URLs as malicious. One Register reader told us: "Our organization has received hundreds of malicious URL alerts from Office 365 for zoom.us links. These false positives take us a long time to investigate. Microsoft finally admitted that this is affecting hundreds of accounts and tenants worldwide."

Microsoft Defender is mistakenly flagging legitimate links as malicious, and some customers have already received dozens of alert emails since the issues began over five hours ago. "We're investigating an issue where legitimate URL links are being incorrectly marked as malicious by the Microsoft Defender service. Additionally, some of the alerts are not showing content as expected," Microsoft said.