Security News

Threat actors with ties to Pakistan have been linked to a long-running malware campaign dubbed Operation Celestial Force since at least 2018. The activity, still ongoing, entails the use of an...

The nascent malware known as SSLoad is being delivered by means of a previously undocumented loader called PhantomLoader, according to findings from cybersecurity firm Intezer. "The loader is...

A previously undocumented cross-platform malware codenamed Noodle RAT has been put to use by Chinese-speaking threat actors either for espionage or cybercrime for years. While this backdoor was...
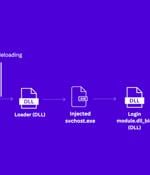
Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that's being distributed as part of a new campaign. "In the latest version, ValleyRAT introduced new...

Cybersecurity researchers have spotted a phishing attack distributing the More_eggs malware by masquerading it as a resume, a technique originally detected more than two years ago. The attack,...

The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting defense forces in the country with a malware called SPECTR as part of an espionage campaign dubbed...

Threat actors are increasingly abusing legitimate and commercially available packer software such as BoxedApp to evade detection and distribute malware such as remote access trojans and...

Sophos released its report, "Operation Crimson Palace: Threat Hunting Unveils Multiple Clusters of Chinese State-Sponsored Activity Targeting Southeast Asia," which details a highly sophisticated, nearly two-year long espionage campaign against a high-level government target. During Sophos X-Ops' investigation, which began in 2023, the managed detection and response team found three distinct clusters of activity targeting the same organization, two of which included tactics, techniques and procedures that overlap with well-known, Chinese nation-state groups: BackdoorDiplomacy, APT15 and the APT41 subgroup Earth Longzhi.

A new report from Cisco Talos exposed the activities of a threat actor known as LilacSquid, or UAT-4820. The threat actor exploits vulnerable web applications or uses compromised Remote Desktop Protection credentials to successfully compromise systems by infecting them with custom PurpleInk malware.
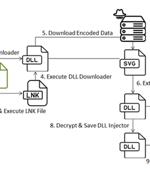
A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per...