Security News
The FBI has recently warned the public about search engine ads pushing malware diguised as legitimate software - an old tactic that has lately resulted in too many malicious ads served to users searching for software, cracked software, drivers - anything that can be downloaded, really - via Google and Bing. The malicious ads often manage to be the first link users see when searching for software on Google, and point to a domain that resembles the original software manufacturer's page.

Hackers are setting up fake websites for popular free and open-source software to promote malicious downloads through advertisements in Google search results. The distribution method was unknown at the time but separate reports in December from cybersecurity companies Trend Micro and Guardio revealed that hackers were abusing the Google Ads platform to push malicious downloads in search results.

Hackers are setting up fake websites for popular free and open-source software to promote malicious downloads through advertisements in Google search results. The distribution method was unknown at the time but separate reports in December from cybersecurity companies Trend Micro and Guardio revealed that hackers were abusing the Google Ads platform to push malicious downloads in search results.

Researchers have demonstrated how threat actors can abuse the GitHub Codespaces' port forwarding' feature to host and distribute malware and malicious scripts. In a new report by Trend Micro, researchers demonstrate how GitHub Codespaces can easily be configured to act as a web server for distributing malicious content while potentially avoiding detection as the traffic comes from Microsoft.

New research has found that it is possible for threat actors to abuse a legitimate feature in GitHub Codespaces to deliver malware to victim systems. "You can also forward a port manually, label forwarded ports, share forwarded ports with members of your organization, share forwarded ports publicly, and add forwarded ports to the codespace configuration," GitHub explains in its documentation.

The packages - named colorslib, httpslib, and libhttps - by the author between January 7, 2023, and January 12, 2023. The modules come with identical setup scripts that are designed to invoke PowerShell and run a malicious binary hosted on Dropbox, Fortinet disclosed in a report published last week.
A threat actor has uploaded to the PyPI repository three malicious packages that carry code to drop info-stealing malware on developers' systems. ' All three have been reported and removed from the PyPI. PyPI is the most widely used repository for Python packages that software developers use to source the building blocks of their projects.
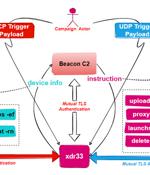
Unidentified threat actors have deployed a new backdoor that borrows its features from the U.S. Central Intelligence Agency's Hive multi-platform malware suite, the source code of which was released by WikiLeaks in November 2017. "This is the first time we caught a variant of the CIA Hive attack kit in the wild, and we named it xdr33 based on its embedded Bot-side certificate CN=xdr33," Qihoo Netlab 360's Alex Turing and Hui Wang said in a technical write-up published last week.

More than 1,600 instances of the Cacti device monitoring tool reachable over the internet are vulnerable to a critical security issue that hackers have already started to exploit. In early December 2022, a security advisory warned of a critical command injection vulnerability in Cacti that could be exploited without authentication.

Hackers breached CircleCi in December after an engineer became infected with information-stealing malware that their 2FA-backed SSO session cookie, allowing access to the company's internal systems. In a new security incident report on the attack, CircleCi says they first learned of the unauthorized access to their systems after a customer reported that their GitHub OAuth token had been compromised.