Security News

Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems. On devices running macOS, Base64-encoded content retrieved from the server is written to a file named "/Users/Shared/AppleAccount.
Microsoft has shared details of a now-patched flaw in Apple macOS that could be abused by threat actors with root access to bypass security enforcements and perform arbitrary actions on affected devices. "The most straight-forward implication of a SIP bypass is that an attacker can create files that are protected by SIP and therefore undeletable by ordinary means," Microsoft researchers Jonathan Bar Or, Michael Pearse, and Anurag Bohra said.

Apple has recently addressed a vulnerability that lets attackers with root privileges bypass System Integrity Protection to install "Undeletable" malware and access the victim's private data by circumventing Transparency, Consent, and Control security checks. Apple has patched the vulnerability in security updates for macOS Ventura 13.4, macOS Monterey 12.6.6, and macOS Big Sur 11.7.7, released two weeks ago, on May 18.

Addigy, makers of mobile device management software MDM Watchdog, released a report today stating that Apple Rapid Security Response updates are not being deployed in about 25% of macOS devices within managed environments. These updates deliver essential security patches between regular software updates and ensure the swift delivery of security updates to devices that run on iOS, iPadOS and macOS. While this strategy is billed to surpass the traditional software update process in terms of speed and efficiency, Addigy has found an unusual scenario that calls for concern.

Geacon, a Go-based implementation of the beacon from the widely abused penetration testing suite Cobalt Strike, is being used more and more to target macOS devices. Both Geacon and Cobalt Strike are utilities that legitimate organizations use to simulate attacks against their networks and improve defenses, but threat actors have also relied on them for attacks.
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems. Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.

Threat actors are advertising a new information stealer for the Apple macOS operating system called Atomic macOS Stealer on Telegram for $1,000 per month, joining the likes of MacStealer. "The Atomic macOS Stealer can steal various types of information from the victim's machine, including Keychain passwords, complete system information, files from the desktop and documents folder, and even the macOS password," Cyble researchers said in a technical report.

A new macOS information-stealing malware named 'Atomic' is being sold to cybercriminals via private Telegram channels for a subscription of $1,000 per month. For this hefty price, buyers get a DMG file containing a 64-bit Go-based malware designed to target macOS systems and steal keychain passwords, files from the local filesystem, passwords, cookies, and credit cards stored in browsers.
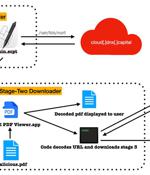
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket. The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.

Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple's macOS operating system.The development, which was reported by the MalwareHunterTeam over the weekend, appears to be the first time a big-game ransomware crew has created a macOS-based payload. Additional samples identified by vx-underground show that the macOS variant has been available since November 11, 2022, and has managed to evade detection by anti-malware engines until now.