Security News

An unknown threat actor is brute-forcing Linux SSH servers to install a wide range of malware, including the Tsunami DDoS bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig coin miner. Network administrators typically use SSH to manage Linux devices remotely, performing tasks such as running commands, changing the configuration, updating software, and troubleshooting problems.

Poorly managed Linux SSH servers are getting compromised by unknown attackers and instructed to engage in DDoS attacks while simultaneously mining cryptocurrency in the background. "The source code of Tsunami is publicly available so it is used by a multitude of threat actors. Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers," researchers with AhnLab's Security Emergency response Center explained.

The threat actor known as ChamelGang has been observed using a previously undocumented implant to backdoor Linux systems, marking a new expansion of the threat actor's capabilities. The malware, dubbed ChamelDoH by Stairwell, is a C++-based tool for communicating via DNS-over-HTTPS tunneling.

The Chinese threat group 'ChamelGang' infects Linux devices with a previously unknown implant named 'ChamelDoH,' allowing DNS-over-HTTPS communications with attackers' servers. The link between ChamelGang and the new Linux malware is based on a domain previously associated with the threat actor and a custom privilege elevation tool observed by Positive Technologies in past ChamelGang campaigns.

The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems. The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867, "Enabled the execution of privileged commands across Windows, Linux, and PhotonOS guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs," Mandiant said.

Hackers are impersonating cybersecurity researchers on Twitter and GitHub to publish fake proof-of-concept exploits for zero-day vulnerabilities that infect Windows and Linux with malware. These malicious exploits are promoted by alleged researchers at a fake cybersecurity company named 'High Sierra Cyber Security,' who promote the GitHub repositories on Twitter, likely to target cybersecurity researchers and firms involved in vulnerability research.

Hackers used the popular Minecraft modding platforms Bukkit and CurseForge to distribute a new 'Fractureiser' information-stealing malware through uploaded modifications and by injecting malicious code into existing projects. According to multiple reports, the attack began when several CurseForge and Bukkit accounts were compromised and used to inject malicious code into plugins and mods, which were then adopted by popular modpacks such as 'Better Minecraft,' which has over 4.6 million downloads.

MOVEit Transfer zero-day attacks: The latest infoProgress Software has updated the security advisory and confirmed that the vulnerability is a SQL injection vulnerability in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer's database. Kali Linux 2023.2 released: New tools, a pre-built Hyper-V image, a new audio stack, and more!Offensive Security has released Kali Linux 2023.2, the latest version of its popular penetration testing and digital forensics platform.
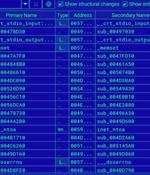
An analysis of the Linux variant of a new ransomware strain called BlackSuit has covered significant similarities with another ransomware family called Royal. Trend Micro, which examined an x64 VMware ESXi version targeting Linux machines, said it identified an "Extremely high degree of similarity" between Royal and BlackSuit.

Kali Linux 2023.2, the second version of 2023, is now available with a pre-built Hyper-V image and thirteen new tools, including the Evilginx framework for stealing credentials and session cookies. As part of the Kali Linux release, the Kali team has released a pre-built Hyper-V image configured for 'Enhanced Session Mode,' which allows you to connect to the virtual machine using the Remote Desktop Protocol for a better experience.