Security News

Erlang? Er, man, no problem. ChatGPT, Claude to go from flaw disclosure to actual attack code in hours The time from vulnerability disclosure to proof-of-concept (PoC) exploit code can now be as...

Cybersecurity researchers have disclosed a critical security flaw in the Lightning AI Studio development platform that, if successfully exploited, could have allowed for remote code execution. The...
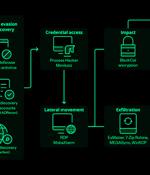
The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals. Active since November 2021, it has emerged as a formidable ransomware actor, victimizing more than 350 targets as of May 2023.

A new and previously undetected malware dubbed 'Lightning Framework' targets Linux systems and can be used to backdoor infected devices using SSH and deploy multiple types of rootkits. Described as a "Swiss Army Knife" in a report published today by Intezer, Lightning Framework is a modular malware that also comes with support for plugins.

Cybersecurity researchers are warning of two different information-stealing malware, named FFDroider and Lightning Stealer, that are capable of siphoning data and launching further attacks. FFDroider is distributed through cracked versions of installers and freeware with the primary objective of stealing cookies and credentials associated with popular social media and e-commerce platforms and using the plundered data to login into the accounts and capture other personal account-related information.

Researchers have discovered a new Python ransomware from an unnamed gang that's striking ESXi servers and virtual machines with what they called "Sniper-like" speed. While the choice of Python for the ransomware is fairly distinctive, going after ESXi servers is anything but.

Normal-looking cables (USB-C, Lightning, and so on) that exfiltrate data over a wireless network. I blogged about a previous prototype here

The team behind Lightning Network has released extensive details on the vulnerabilities that were discovered in the cryptocurrency protocol and its software implementations. Attackers could have exploited these vulnerabilities to cause DoS and to disrupt crypto transactions by intercepting "Smart contracts" made between two parties.

The analysis of the attack revealed that after about four hours and 10 minutes, the Ryuk gang pivoted from the primary domain controller, using RDP to connect to backup servers. For the final phase of the attack, the Ryuk operators first deployed their ransomware executable onto backup servers.

This malicious O.MG Lightning cable has come a long way, with extensive work on the kinds of payload it can deliver.