Security News

Unclear if this is a sign controversial service is cleaning up its act everywhere Controversial social network Telegram has co-operated with South Korean authorities and taken down 25 videos...

A newly patched security flaw in Microsoft Windows was exploited as a zero-day by Lazarus Group, a prolific state-sponsored actor affiliated with North Korea. The security vulnerability, tracked...

South Korea's ruling party, People Power Party (PPP), has issued an announcement stating that North Korean hackers have stolen crucial information about K2 tanks, the country's main battle tank,...

The FBI today arrested a Tennessee man suspected of running a "Laptop farm" that got North Koreans, posing as Westerners, IT jobs at American and British companies. According to US prosecutors, Matthew Isaac Knoot, 38, of Nashville, defrauded multiple US and UK companies by applying for remote technology jobs, and then secretly outsourced those jobs to North Koreans.
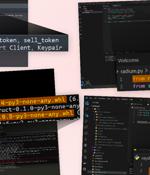
The threat actors behind an ongoing malware campaign targeting software developers have demonstrated new malware and tactics, expanding their focus to include Windows, Linux, and macOS systems. DEV#POPPER is the moniker assigned to an active malware campaign that tricks software developers into downloading booby-trapped software hosted on GitHub under the guise of a job interview.

Indian crypto exchange WazirX has revealed it lost virtual assets valued at over $230 million after a cyber attack that has since been linked to North Korea. According to a late Thursday WazirX Xeet, the attack targeted one of its multi-signature wallets - digi-cash lockers that are designed to offer superior security by requiring multiple private keys to authorize a transaction.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The U.S. Justice Department charged five individuals today, a U.S. Citizen woman, a Ukrainian man, and three foreign nationals, for their involvement in cyber schemes that generated revenue for North Korea's nuclear weapons program. They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government "To infiltrate U.S. job markets through fraud in an effort to raise revenue for the North Korean government and its illicit nuclear program."

The U.S. Justice Department charged five individuals today, a U.S. Citizen woman, a Ukrainian man, and three foreign nationals, for their involvement in cyber schemes that generated revenue for North Korea's nuclear weapons program. They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government "To infiltrate U.S. job markets through fraud in an effort to raise revenue for the North Korean government and its illicit nuclear program."

The U.S. Justice Department charged five individuals today, a U.S. Citizen woman, a Ukrainian man, and three foreign nationals, for their involvement in cyber schemes that generated revenue for North Korea's nuclear weapons program. They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government "To infiltrate U.S. job markets through fraud in an effort to raise revenue for the North Korean government and its illicit nuclear program."